Protect your businesss most valuable assets with the Crown Jewel Defense Strategy. Learn how to identify, prioritize, and safeguard your crown jewels from cyber threats. Discover 5 effective ways to implement this strategy, including risk assessment, threat modeling, and incident response planning.
In today's fast-paced and ever-evolving business landscape, organizations face numerous threats to their most valuable assets. One strategy that has gained popularity in recent years is the Crown Jewel Defense (CJD) approach. This strategy focuses on protecting an organization's most critical assets, referred to as its "crown jewels," by implementing a robust defense mechanism. In this article, we will explore five ways to implement a Crown Jewel Defense strategy effectively.
Understanding Crown Jewel Defense Strategy

The CJD approach is designed to protect an organization's most valuable assets, which can include intellectual property, customer data, financial information, or any other critical resource. This strategy is particularly useful for organizations that have a large number of assets to protect, as it allows them to prioritize their defense efforts on the most critical ones.
Benefits of Crown Jewel Defense Strategy
- Enhanced security for critical assets
- Improved incident response and remediation
- Increased visibility into security threats
- Better resource allocation for security efforts
- Reduced risk of data breaches and cyber attacks
1. Identify Your Crown Jewels

The first step in implementing a CJD strategy is to identify your organization's crown jewels. This involves conducting a thorough risk assessment to determine which assets are most critical to your business. You should consider factors such as the asset's value, sensitivity, and potential impact on your business if compromised.
Factors to Consider When Identifying Crown Jewels
- Value: How valuable is the asset to your business?
- Sensitivity: How sensitive is the asset, and what are the potential consequences if it is compromised?
- Impact: What would be the impact on your business if the asset is compromised or lost?
2. Assess Your Current Security Posture

Once you have identified your crown jewels, you need to assess your current security posture to determine the effectiveness of your existing security controls. This involves conducting a thorough security audit to identify vulnerabilities and weaknesses in your security infrastructure.
Steps to Assess Your Security Posture
- Conduct a security audit to identify vulnerabilities and weaknesses
- Review your existing security controls and policies
- Identify gaps in your security posture
- Develop a plan to address identified gaps and weaknesses
3. Develop a Defense-in-Depth Strategy

A defense-in-depth strategy involves implementing multiple layers of security controls to protect your crown jewels. This approach ensures that even if one security control is compromised, others can still provide protection.
Layers of Defense-in-Depth Strategy
- Network security: Implement firewalls, intrusion detection systems, and network segmentation
- Endpoint security: Implement antivirus software, endpoint detection and response tools, and encryption
- Application security: Implement secure coding practices, vulnerability management, and application firewalls
- Data security: Implement encryption, access controls, and data loss prevention tools
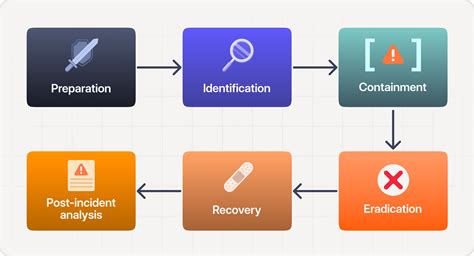
4. Implement Incident Response and Remediation
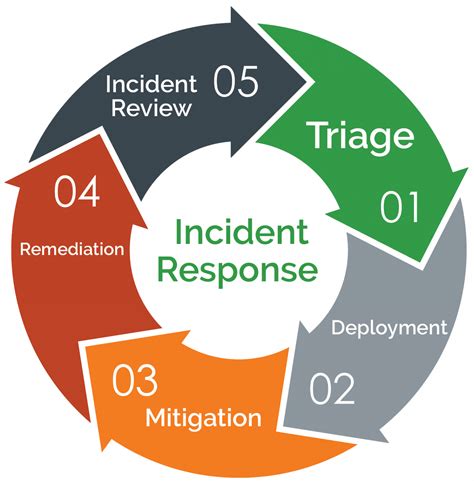
Incident response and remediation are critical components of a CJD strategy. You need to have a plan in place to respond quickly and effectively in the event of a security incident.
Steps to Implement Incident Response and Remediation
- Develop an incident response plan that outlines roles and responsibilities
- Establish communication protocols for incident response
- Conduct regular training and exercises to ensure preparedness
- Continuously review and update your incident response plan
5. Continuously Monitor and Improve
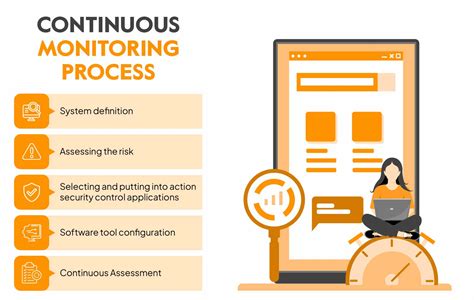
Finally, you need to continuously monitor and improve your CJD strategy to ensure it remains effective. This involves regularly reviewing your security posture, identifying new threats, and updating your security controls accordingly.
Steps to Continuously Monitor and Improve
- Regularly review your security posture and identify areas for improvement
- Stay up-to-date with emerging threats and vulnerabilities
- Continuously update and refine your security controls
- Conduct regular security audits and risk assessments
Crown Jewel Defense Strategy Image Gallery






By following these five steps, you can implement a Crown Jewel Defense strategy that effectively protects your organization's most valuable assets.
