Intro
Discover the crucial roles of a Cyber Security Specialist in protecting networks, systems, and data from cyber threats. Learn about the 5 key responsibilities, including threat analysis, vulnerability assessment, security measures implementation, incident response, and compliance monitoring, to stay ahead of hackers and ensure a secure digital landscape.
As the world becomes increasingly reliant on technology, the threat of cyber attacks and data breaches continues to grow. Cyber security specialists play a crucial role in protecting individuals, businesses, and organizations from these threats. In this article, we will explore the 5 key responsibilities of a cyber security specialist and delve into the details of each responsibility.

Protecting Computer Systems and Networks
Cyber security specialists are responsible for protecting computer systems and networks from cyber threats. This includes installing and configuring security software, such as firewalls and antivirus programs, to prevent unauthorized access to sensitive data. They must also monitor systems and networks for signs of suspicious activity and respond quickly to any incidents that may occur.
Some of the specific tasks involved in this responsibility include:
- Conducting regular security audits to identify vulnerabilities
- Implementing security measures, such as encryption and access controls
- Monitoring system logs to detect potential security breaches
- Responding to security incidents, such as viruses and malware attacks
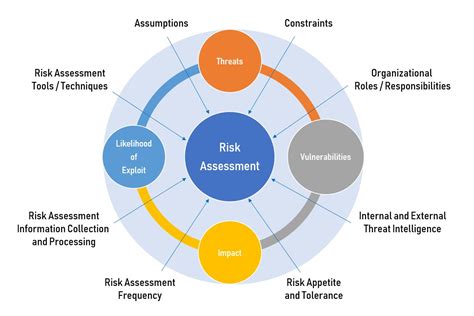
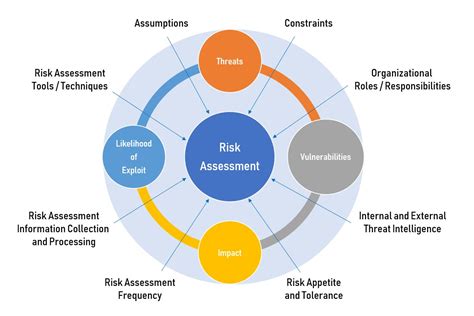
Conducting Risk Assessments and Vulnerability Testing
Cyber security specialists must also conduct risk assessments and vulnerability testing to identify potential security threats. This involves analyzing systems and networks to identify vulnerabilities and weaknesses, and then prioritizing remediation efforts based on the level of risk.
Some of the specific tasks involved in this responsibility include:
- Conducting regular vulnerability scans to identify potential weaknesses
- Analyzing system logs to identify potential security threats
- Prioritizing remediation efforts based on the level of risk
- Implementing measures to mitigate identified risks
Developing and Implementing Security Policies
Cyber security specialists are responsible for developing and implementing security policies to ensure that an organization's computer systems and networks are secure. This includes creating policies and procedures for data protection, access control, and incident response.
Some of the specific tasks involved in this responsibility include:
- Developing security policies and procedures
- Conducting security awareness training for employees
- Monitoring compliance with security policies
- Updating security policies to reflect changes in the threat landscape
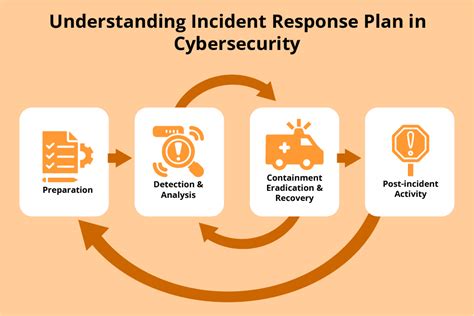
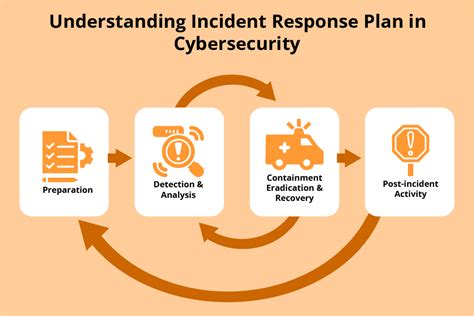
Investigating Security Incidents
Cyber security specialists must also investigate security incidents, such as data breaches and malware attacks, to determine the cause and impact of the incident. This involves analyzing system logs and other data to identify the source of the incident and developing strategies to prevent similar incidents in the future.
Some of the specific tasks involved in this responsibility include:
- Analyzing system logs to identify the source of a security incident
- Conducting forensic analysis to determine the cause and impact of the incident
- Developing strategies to prevent similar incidents in the future
- Providing incident response training to employees
Staying Up-to-Date with Emerging Threats
Finally, cyber security specialists must stay up-to-date with emerging threats and technologies to ensure that they are prepared to respond to new and evolving threats. This includes attending conferences and training sessions, participating in online forums and discussions, and reading industry publications.
Some of the specific tasks involved in this responsibility include:
- Attending conferences and training sessions to stay current with emerging threats
- Participating in online forums and discussions to share knowledge and best practices
- Reading industry publications to stay informed about new threats and technologies
- Developing strategies to mitigate the risks associated with emerging threats

Conclusion and Next Steps
In conclusion, the role of a cyber security specialist is critical in protecting individuals, businesses, and organizations from cyber threats. By understanding the 5 key responsibilities of a cyber security specialist, organizations can take steps to ensure that their computer systems and networks are secure.
If you are interested in pursuing a career in cyber security, there are many resources available to help you get started. Some options include:
- Pursuing a degree in cyber security or a related field
- Obtaining certifications, such as CompTIA Security+ or CISSP
- Participating in online forums and discussions to stay current with emerging threats
- Attending conferences and training sessions to stay informed about new threats and technologies
We hope this article has provided you with a comprehensive understanding of the 5 key responsibilities of a cyber security specialist. If you have any questions or comments, please feel free to share them below.
Cyber Security Specialist Image Gallery