Intro
In today's digital age, cyber security is a top priority for individuals and organizations alike. With the ever-increasing threat of cyber attacks, it's essential to have a robust defense system in place to protect sensitive information and prevent financial losses. One effective way to boost protection is by using cyber security templates. These templates provide a framework for implementing security measures, identifying potential threats, and responding to incidents. In this article, we'll explore seven essential cyber security templates to help you enhance your protection.
Understanding the Importance of Cyber Security Templates
Cyber security templates are pre-designed documents that outline the procedures and protocols for managing cyber security risks. They help organizations establish a systematic approach to security, ensuring that all employees are on the same page. By using these templates, you can save time, reduce costs, and improve your overall security posture.
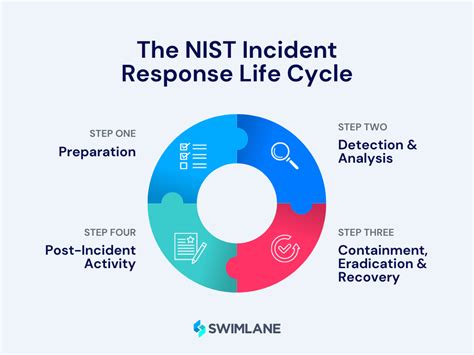
Template 1: Incident Response Plan
An incident response plan is a critical template that outlines the procedures for responding to a cyber security incident. This plan should include:
- Incident classification and reporting procedures
- Incident response team roles and responsibilities
- Communication protocols for stakeholders and employees
- Incident containment and eradication procedures
- Post-incident activities and lessons learned
Having a well-structured incident response plan in place can help minimize the impact of a security breach and reduce downtime.
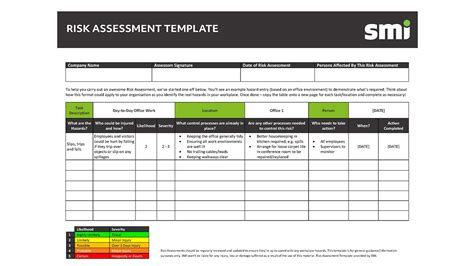
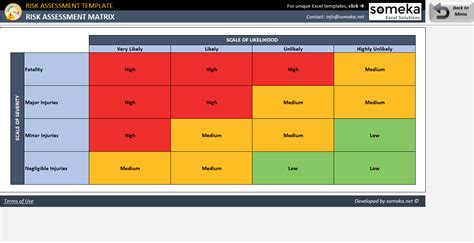
Template 2: Risk Assessment Template
A risk assessment template is used to identify, assess, and prioritize potential security risks. This template should include:
- Risk identification and categorization
- Risk assessment criteria (e.g., likelihood, impact, and vulnerability)
- Risk mitigation strategies and recommendations
- Risk monitoring and review procedures
Regular risk assessments can help you stay ahead of potential threats and ensure that your security controls are effective.
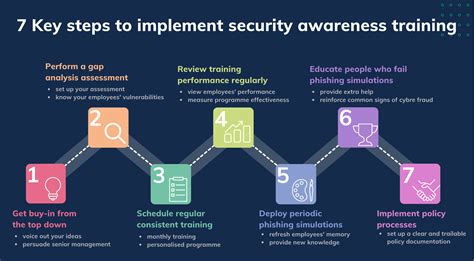
Template 3: Security Awareness Training Program
A security awareness training program template is designed to educate employees on cyber security best practices and phishing attacks. This template should include:
- Training objectives and scope
- Target audience and training frequency
- Training content (e.g., security policies, password management, and safe browsing habits)
- Training delivery methods (e.g., online modules, workshops, and quizzes)
Regular security awareness training can help reduce the risk of human error and improve your organization's overall security posture.
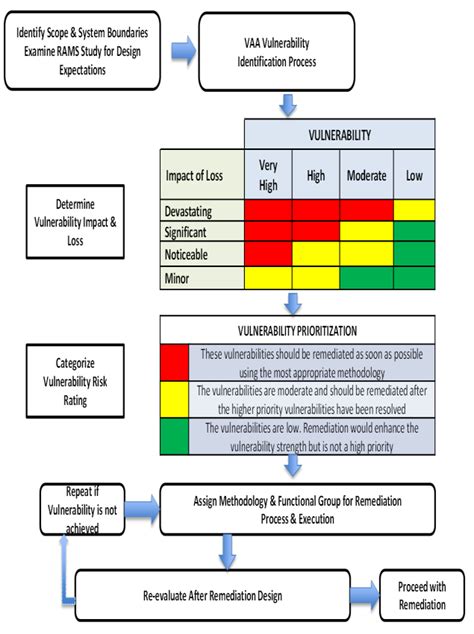
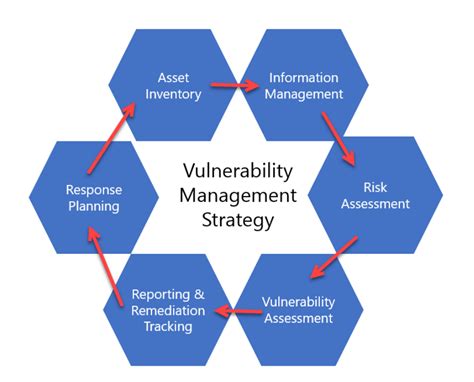
Template 4: Vulnerability Management Template
A vulnerability management template is used to identify, prioritize, and remediate vulnerabilities in your systems and applications. This template should include:
- Vulnerability scanning and detection procedures
- Vulnerability classification and prioritization
- Remediation strategies and recommendations
- Vulnerability monitoring and review procedures
Regular vulnerability management can help you stay on top of potential security risks and prevent attacks.
Template 5: Compliance Template
A compliance template is designed to help organizations meet regulatory requirements and industry standards. This template should include:
- Compliance scope and objectives
- Regulatory requirements and industry standards
- Compliance procedures and protocols
- Compliance monitoring and review procedures
Using a compliance template can help you ensure that your organization meets the necessary regulatory requirements and avoids costly fines.

Template 6: Penetration Testing Template
A penetration testing template is used to simulate cyber attacks on your systems and applications. This template should include:
- Penetration testing objectives and scope
- Testing methodologies and procedures
- Vulnerability exploitation and reporting
- Remediation strategies and recommendations
Regular penetration testing can help you identify vulnerabilities and improve your overall security posture.

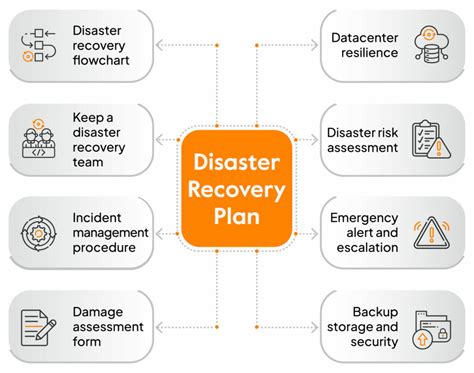
Template 7: Disaster Recovery Plan
A disaster recovery plan template is designed to help organizations recover from a disaster or major outage. This template should include:
- Disaster recovery objectives and scope
- Disaster classification and declaration procedures
- Recovery procedures and protocols
- Post-disaster review and lessons learned
Having a well-structured disaster recovery plan in place can help minimize downtime and ensure business continuity.

Cyber Security Templates Gallery
Cyber Security Templates Gallery






In conclusion, cyber security templates are essential tools for boosting protection in today's digital age. By using these templates, you can establish a systematic approach to security, identify potential threats, and respond to incidents effectively. Remember to regularly review and update your templates to ensure that your organization stays ahead of the ever-evolving cyber security landscape.
We hope this article has provided you with valuable insights into the world of cyber security templates. If you have any questions or would like to share your experiences with using these templates, please leave a comment below. Don't forget to share this article with your colleagues and friends to help spread awareness about the importance of cyber security.
