Discover the cutting-edge tactics used by the Air Force to conduct cyber warfare operations. Learn about the 5 key ways they employ cyber warfare to safeguard national security, including network exploitation, vulnerability assessment, and electronic warfare. Understand the crucial role of cyber warfare in modern military strategy and stay ahead of the threat landscape.
Cyber warfare has become a critical component of modern military operations, and the Air Force is at the forefront of this effort. As the world becomes increasingly reliant on digital technologies, the need to protect and defend against cyber threats has never been more pressing. In this article, we will explore five ways the Air Force conducts cyber warfare operations.
Cyber Warfare Operations: A Growing Need
In today's digital age, cyber threats are becoming more sophisticated and frequent. Nation-states, terrorist organizations, and rogue actors are increasingly using cyber attacks to disrupt critical infrastructure, steal sensitive information, and undermine national security. The Air Force recognizes the importance of cyber warfare and has been investing heavily in its cyber capabilities.
1. Network Defense Operations
The Air Force's cyber warfare operations begin with network defense. This involves protecting Air Force networks and systems from cyber threats, including malware, phishing attacks, and unauthorized access attempts. The Air Force uses a range of tools and techniques to detect and respond to these threats, including firewalls, intrusion detection systems, and security information and event management (SIEM) systems.

2. Offensive Cyber Operations
In addition to defending its own networks, the Air Force also conducts offensive cyber operations. This involves using cyber attacks to disrupt or destroy an adversary's command and control systems, disrupting their ability to communicate and coordinate. The Air Force uses a range of tactics, techniques, and procedures (TTPs) to conduct these operations, including network exploitation, malware, and denial-of-service attacks.
Key Components of Offensive Cyber Operations
- Network exploitation: This involves using cyber attacks to gain unauthorized access to an adversary's networks and systems.
- Malware: This involves using malicious software to disrupt or destroy an adversary's systems.
- Denial-of-service attacks: This involves overwhelming an adversary's systems with traffic in order to make them unavailable.
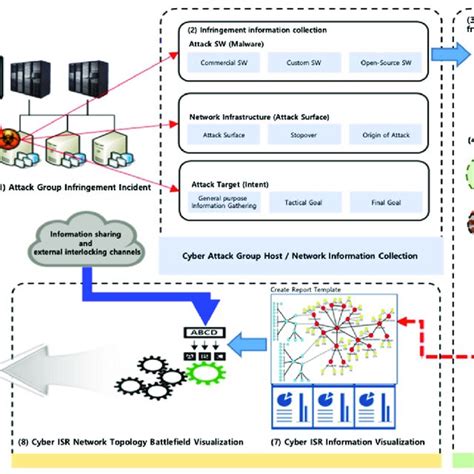
3. Cyber Intelligence, Surveillance, and Reconnaissance (ISR)
The Air Force also conducts cyber ISR operations to gather intelligence on potential adversaries. This involves using cyber sensors and other tools to collect and analyze data on an adversary's cyber activities. The Air Force uses this intelligence to inform its cyber operations and to stay one step ahead of emerging threats.
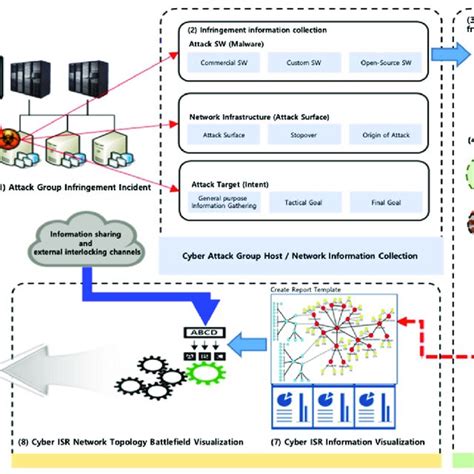
4. Cyber Support to Kinetic Operations
The Air Force also provides cyber support to kinetic operations. This involves using cyber attacks to disrupt an adversary's command and control systems, creating an advantage for Air Force kinetic operations. The Air Force uses a range of tactics and techniques to conduct these operations, including network exploitation and denial-of-service attacks.
Key Benefits of Cyber Support to Kinetic Operations
- Enhanced situational awareness: Cyber ISR provides critical intelligence on an adversary's cyber activities, enhancing situational awareness and informing kinetic operations.
- Disruption of adversary command and control: Cyber attacks can disrupt an adversary's command and control systems, creating an advantage for Air Force kinetic operations.
5. Cybersecurity Collaboration and Information Sharing
Finally, the Air Force recognizes the importance of collaboration and information sharing in cyber warfare operations. The Air Force works closely with other military services, government agencies, and industry partners to share threat intelligence and best practices. This collaboration enables the Air Force to stay ahead of emerging threats and to improve its cyber defenses.
Gallery of Air Force Cyber Warfare Operations
Air Force Cyber Warfare Operations Image Gallery







Final Thoughts
The Air Force's cyber warfare operations are a critical component of its overall mission. By conducting network defense operations, offensive cyber operations, cyber ISR, cyber support to kinetic operations, and cybersecurity collaboration and information sharing, the Air Force is able to stay ahead of emerging threats and protect national security. As the world becomes increasingly reliant on digital technologies, the importance of cyber warfare operations will only continue to grow.
