Intro
Protect your organizations sensitive data with a comprehensive data security plan. Learn the 5 essential steps to safeguard against cyber threats, including risk assessment, policy development, and incident response. Discover how to implement a robust data security strategy that ensures compliance and minimizes data breaches, data loss, and cyber attacks.
In today's digital age, data security is a top concern for businesses, organizations, and individuals alike. With the increasing amount of sensitive information being stored and transmitted online, the risk of data breaches and cyber attacks has become a looming threat. A data security plan is essential to protect your organization's sensitive information from unauthorized access, theft, and destruction. In this article, we will outline the 5 essential steps to create a comprehensive data security plan.

Understanding the Importance of Data Security
Before we dive into the 5 essential steps, it's crucial to understand the importance of data security. Data security refers to the practices and technologies used to protect sensitive information from unauthorized access, theft, and destruction. This includes personal identifiable information (PII), financial data, intellectual property, and confidential business information. A data security plan helps to identify, assess, and mitigate potential risks and vulnerabilities, ensuring the confidentiality, integrity, and availability of sensitive information.
Step 1: Identify and Classify Sensitive Data
The first step in creating a data security plan is to identify and classify sensitive data. This involves determining what data is sensitive, where it is stored, and how it is transmitted. Sensitive data can include PII, financial data, intellectual property, and confidential business information. Once you have identified the sensitive data, classify it based on its level of sensitivity and importance to the organization. This will help you determine the level of protection required for each type of data.
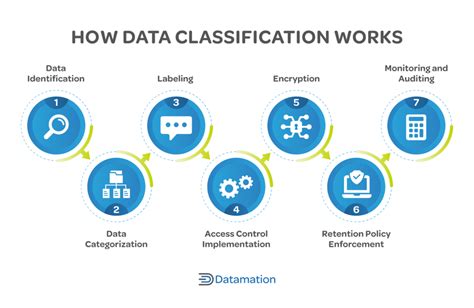
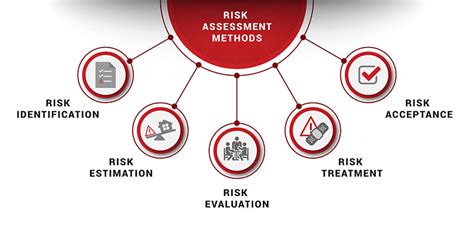
Step 2: Assess Risks and Vulnerabilities
The second step is to assess risks and vulnerabilities associated with sensitive data. This involves identifying potential threats, such as cyber attacks, data breaches, and insider threats. Conduct a risk assessment to determine the likelihood and impact of each threat. This will help you prioritize your security efforts and allocate resources effectively.
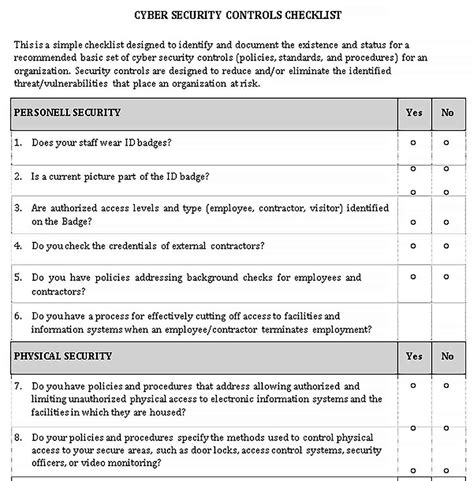
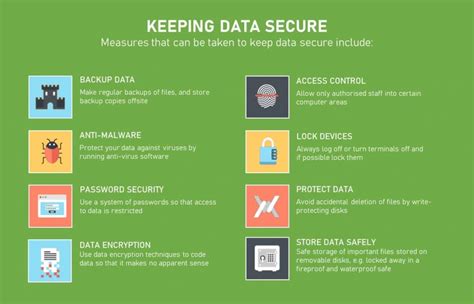
Step 3: Implement Security Controls
The third step is to implement security controls to protect sensitive data. This includes:
- Access controls: Limit access to sensitive data to authorized personnel only.
- Encryption: Encrypt sensitive data both in transit and at rest.
- Firewalls: Install firewalls to block unauthorized access to the network.
- Intrusion detection: Install intrusion detection systems to detect and respond to potential threats.
- Backup and recovery: Implement a backup and recovery process to ensure business continuity in the event of a disaster.
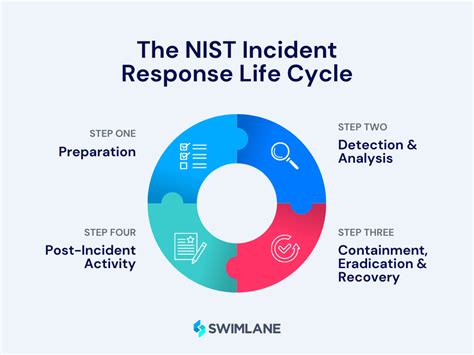
Step 4: Monitor and Incident Response
The fourth step is to monitor and respond to security incidents. This involves:
- Monitoring: Continuously monitor the network and systems for potential security threats.
- Incident response: Establish an incident response plan to respond to security incidents quickly and effectively.
- Reporting: Report security incidents to relevant authorities and stakeholders.
Step 5: Continuously Review and Update
The fifth and final step is to continuously review and update the data security plan. This involves:
- Regular reviews: Regularly review the data security plan to ensure it remains effective and up-to-date.
- Update policies: Update policies and procedures to reflect changes in the organization and new security threats.
- Training and awareness: Provide training and awareness programs to ensure employees understand the importance of data security and their roles in protecting sensitive information.
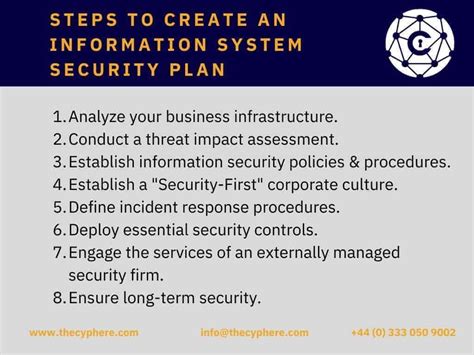
Data Security Plan Gallery

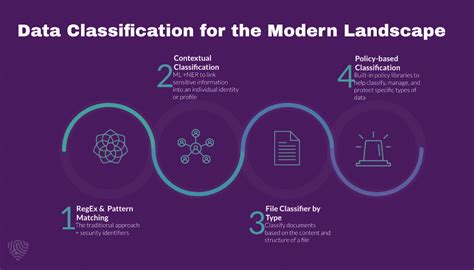



By following these 5 essential steps, you can create a comprehensive data security plan that protects your organization's sensitive information from unauthorized access, theft, and destruction. Remember to continuously review and update your plan to ensure it remains effective and up-to-date.
We hope this article has provided you with valuable insights into creating a data security plan. If you have any questions or comments, please feel free to share them below.
