Intro
Boost your digital defense with expert insights on Cyber Security in IT. Learn how to protect your digital assets from cyber threats, including data breaches, malware, and phishing attacks. Discover the latest security strategies, threat prevention measures, and best practices to safeguard your online presence and ensure business continuity.
In today's digital age, technology plays a vital role in the way we live, work, and communicate. As we increasingly rely on digital platforms to store and manage our personal and professional data, the importance of cyber security in IT cannot be overstated. The threat of cyber attacks and data breaches is ever-present, and the consequences of a security breach can be devastating. From financial loss to reputational damage, the risks associated with inadequate cyber security measures are simply too great to ignore.
The impact of a cyber attack can be far-reaching, affecting not only individuals but also businesses and organizations of all sizes. In recent years, we have seen a significant increase in the number of high-profile data breaches, with major companies and institutions falling victim to sophisticated cyber attacks. These attacks have resulted in the theft of sensitive data, including financial information, personal identifiable information, and confidential business data. The consequences of these breaches have been severe, with many organizations facing significant financial losses, damage to their reputation, and even legal action.
As the threat of cyber attacks continues to grow, it is essential that individuals and organizations take proactive steps to protect their digital assets. This requires a comprehensive approach to cyber security, one that includes a range of measures designed to prevent, detect, and respond to cyber threats.
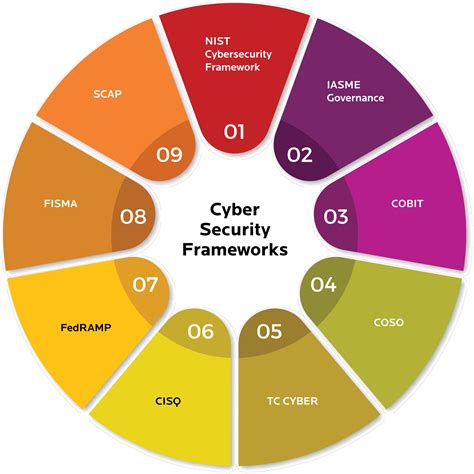
Understanding Cyber Security Threats

Before we can develop effective strategies for protecting our digital assets, it is essential that we understand the nature of the threats we face. Cyber security threats can take many forms, including:
- Malware: Malicious software designed to harm or exploit a computer system.
- Phishing: Social engineering attacks designed to trick individuals into divulging sensitive information.
- Ransomware: Malware that encrypts a victim's data and demands payment in exchange for the decryption key.
- DDoS attacks: Distributed denial-of-service attacks designed to overwhelm a computer system or network.
- SQL injection: Attacks designed to exploit vulnerabilities in databases and extract sensitive data.
Types of Cyber Attacks
Cyber attacks can be broadly classified into several categories, including:
- Network attacks: Attacks that target computer networks, including DDoS attacks and malware.
- Application attacks: Attacks that target software applications, including SQL injection and cross-site scripting (XSS).
- Data attacks: Attacks that target sensitive data, including phishing and ransomware.
- Physical attacks: Attacks that target physical devices, including laptops, smartphones, and servers.
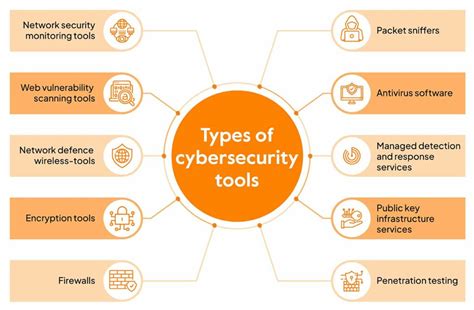
Protecting Your Digital Assets

Protecting your digital assets requires a comprehensive approach to cyber security, one that includes a range of measures designed to prevent, detect, and respond to cyber threats. Some of the key measures you can take to protect your digital assets include:
- Implementing firewalls and intrusion detection systems: Firewalls and intrusion detection systems can help to prevent unauthorized access to your computer systems and networks.
- Using anti-virus software: Anti-virus software can help to prevent malware infections and detect and remove malicious software.
- Encrypting sensitive data: Encrypting sensitive data can help to protect it from unauthorized access.
- Using strong passwords: Using strong passwords can help to prevent unauthorized access to your computer systems and networks.
- Implementing a incident response plan: An incident response plan can help to ensure that you are prepared to respond to a cyber attack.
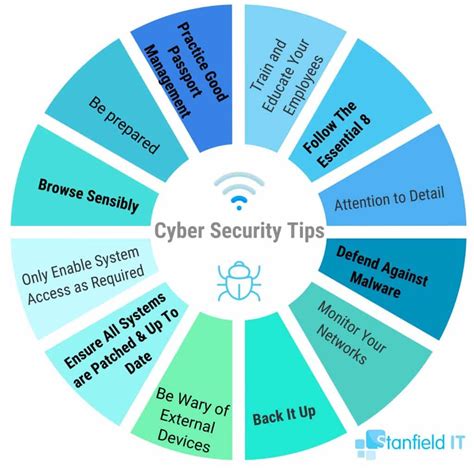
Best Practices for Cyber Security
In addition to implementing the measures outlined above, there are several best practices you can follow to help protect your digital assets, including:
- Keeping software up-to-date: Keeping software up-to-date can help to ensure that you have the latest security patches and updates.
- Using two-factor authentication: Using two-factor authentication can help to prevent unauthorized access to your computer systems and networks.
- Monitoring system logs: Monitoring system logs can help to detect and respond to cyber threats.
- Providing employee training: Providing employee training can help to ensure that your employees are aware of the risks associated with cyber attacks and know how to respond.
Cyber Security in the Cloud

As more and more organizations move their data and applications to the cloud, the importance of cyber security in the cloud cannot be overstated. Cloud computing offers many benefits, including increased flexibility, scalability, and cost savings. However, it also introduces new cyber security risks, including:
- Data breaches: Data breaches can occur when unauthorized individuals gain access to sensitive data stored in the cloud.
- Denial of service attacks: Denial of service attacks can occur when an attacker attempts to overwhelm a cloud-based system or network.
- Malware: Malware can be used to attack cloud-based systems and networks.
To protect your digital assets in the cloud, it is essential that you take a comprehensive approach to cyber security, one that includes a range of measures designed to prevent, detect, and respond to cyber threats.
Cloud Cyber Security Best Practices
Some of the key best practices for cloud cyber security include:
- Using cloud security gateways: Cloud security gateways can help to prevent unauthorized access to your cloud-based systems and networks.
- Implementing encryption: Implementing encryption can help to protect sensitive data stored in the cloud.
- Using two-factor authentication: Using two-factor authentication can help to prevent unauthorized access to your cloud-based systems and networks.
- Monitoring system logs: Monitoring system logs can help to detect and respond to cyber threats.
Cyber Security and Compliance

In addition to protecting your digital assets from cyber threats, it is also essential that you comply with relevant laws and regulations related to cyber security. Some of the key laws and regulations related to cyber security include:
- General Data Protection Regulation (GDPR): The GDPR is a comprehensive data protection regulation that applies to all organizations that collect, store, and process personal data of EU citizens.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA is a federal law that regulates the use and disclosure of protected health information.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards designed to ensure that companies that handle credit card information maintain a secure environment.
To ensure compliance with these laws and regulations, it is essential that you implement a comprehensive cyber security program that includes measures designed to prevent, detect, and respond to cyber threats.
Cyber Security Compliance Best Practices
Some of the key best practices for cyber security compliance include:
- Conducting regular risk assessments: Conducting regular risk assessments can help to identify potential cyber security risks and ensure that you are in compliance with relevant laws and regulations.
- Implementing incident response plans: Implementing incident response plans can help to ensure that you are prepared to respond to a cyber attack.
- Providing employee training: Providing employee training can help to ensure that your employees are aware of the risks associated with cyber attacks and know how to respond.
Conclusion
Cyber security is a critical aspect of IT that requires a comprehensive approach to protecting your digital assets from cyber threats. By understanding the nature of the threats you face, implementing measures designed to prevent, detect, and respond to cyber threats, and complying with relevant laws and regulations, you can help to ensure the security and integrity of your digital assets.
Cyber Security Image Gallery







We hope you found this article informative and helpful. If you have any questions or comments, please feel free to share them with us.
