Intro
Unlock the complexities of cyber security with our expert insights. Discover the 7 reasons why cyber security can be challenging, from evolving threats and sophisticated attacks to human error and inadequate training. Learn how to overcome these obstacles and protect your digital assets with effective cyber security measures.
Cyber security is a critical aspect of modern life, as technology advances and more aspects of our lives move online. However, protecting ourselves and our organizations from cyber threats can be a daunting task. With the increasing complexity of technology and the evolving nature of threats, cyber security can be challenging. In this article, we will explore seven reasons why cyber security can be challenging and what can be done to address these challenges.
Reason 1: Increasing Complexity of Technology

One of the primary reasons cyber security can be challenging is the increasing complexity of technology. As technology advances, more devices and systems become connected, creating a vast attack surface for cyber threats. The Internet of Things (IoT), for example, has introduced a plethora of new devices that can be exploited by attackers. Furthermore, the complexity of modern software and systems makes it difficult to identify and patch vulnerabilities.
Addressing Complexity with Simplification
To address the complexity of technology, organizations can simplify their systems and networks. This can be achieved by implementing a zero-trust architecture, where access to resources is restricted by default, and only granted when necessary. Additionally, organizations can adopt a microservices architecture, where applications are broken down into smaller, more manageable components.
Reason 2: Evolving Nature of Threats

Cyber threats are constantly evolving, with new threats emerging every day. From phishing and ransomware to advanced persistent threats (APTs) and nation-state attacks, the threat landscape is vast and complex. The evolving nature of threats makes it challenging for organizations to stay ahead of the curve and protect themselves against the latest threats.
Staying Ahead of Threats with Threat Intelligence
To stay ahead of the evolving nature of threats, organizations can adopt a threat intelligence-driven approach to cyber security. This involves gathering and analyzing data on threats, as well as sharing intelligence with other organizations and governments. By staying informed about the latest threats, organizations can better protect themselves against emerging threats.
Reason 3: Human Error
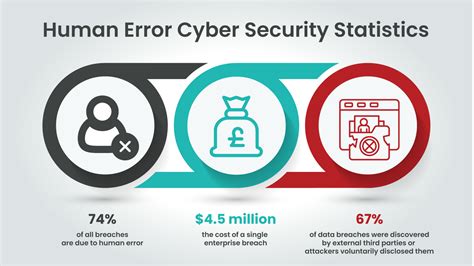
Human error is a significant contributor to cyber security breaches. Whether it's a employee clicking on a phishing email or an administrator accidentally misconfiguring a firewall, human error can have devastating consequences. The problem is that humans are inherently fallible, and mistakes can happen even with the best intentions.
Addressing Human Error with Training and Awareness
To address human error, organizations can implement training and awareness programs to educate employees on cyber security best practices. This can include regular phishing simulations, as well as training on how to handle sensitive data and configure systems securely.
Reason 4: Resource Constraints
Cyber security requires significant resources, including personnel, budget, and technology. However, many organizations face resource constraints, making it challenging to implement effective cyber security measures. This can be particularly challenging for small and medium-sized businesses (SMBs), which may not have the resources to invest in cyber security.
Addressing Resource Constraints with Prioritization
To address resource constraints, organizations can prioritize their cyber security efforts. This involves identifying the most critical assets and systems, and allocating resources accordingly. Additionally, organizations can adopt a risk-based approach to cyber security, where resources are allocated based on the level of risk.
Reason 5: Lack of Visibility
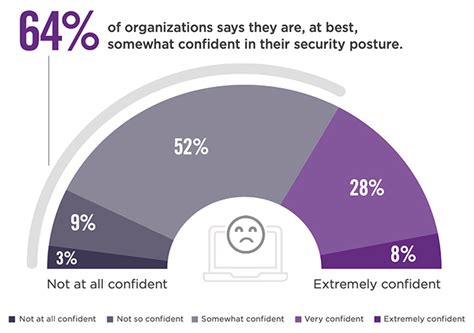
Lack of visibility is a significant challenge in cyber security. With the increasing complexity of technology, it's becoming more difficult to monitor and detect threats in real-time. This can lead to delays in detecting and responding to breaches, which can have devastating consequences.
Addressing Lack of Visibility with Monitoring and Analytics
To address lack of visibility, organizations can implement monitoring and analytics tools to detect and respond to threats in real-time. This can include implementing a security information and event management (SIEM) system, as well as using machine learning and artificial intelligence to analyze logs and detect anomalies.
Reason 6: Compliance and Regulatory Challenges

Compliance and regulatory challenges are a significant aspect of cyber security. With the increasing number of regulations and standards, organizations must ensure that they comply with the relevant regulations and standards. However, compliance and regulatory challenges can be complex and time-consuming, making it challenging for organizations to focus on cyber security.
Addressing Compliance and Regulatory Challenges with a Framework
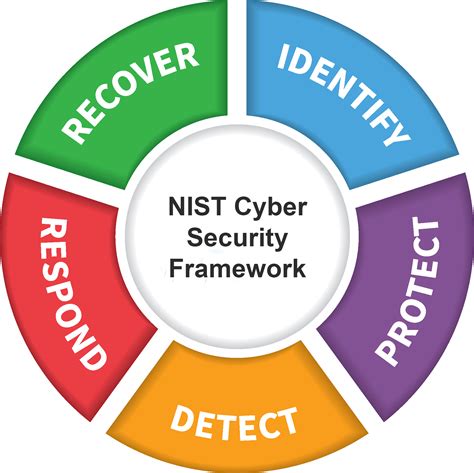
To address compliance and regulatory challenges, organizations can adopt a framework-based approach to cyber security. This involves implementing a framework such as the NIST Cybersecurity Framework, which provides a structured approach to managing cyber security.
Reason 7: Insider Threats
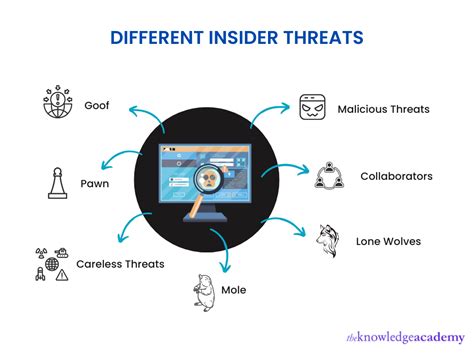
Insider threats are a significant challenge in cyber security. Whether it's a disgruntled employee or a compromised administrator account, insider threats can have devastating consequences. The problem is that insider threats are often difficult to detect, as they come from within the organization.
Addressing Insider Threats with Monitoring and Detection
To address insider threats, organizations can implement monitoring and detection tools to identify and respond to insider threats. This can include implementing a user and entity behavior analytics (UEBA) system, as well as using machine learning and artificial intelligence to detect anomalies.
Cyber Security Challenges Image Gallery
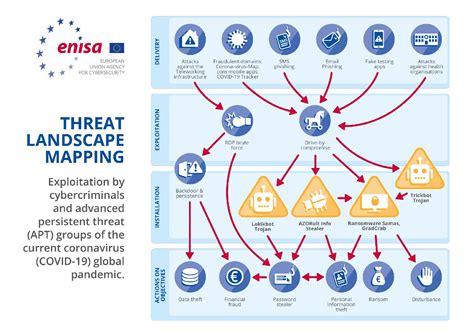
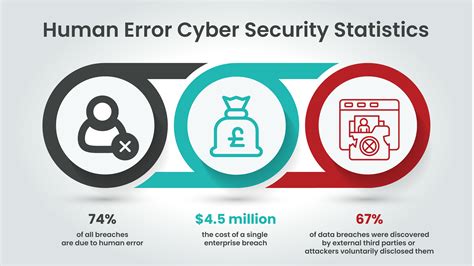
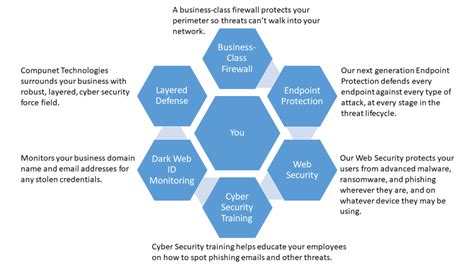





Cyber security is a complex and challenging field, with many different threats and challenges to navigate. However, by understanding the reasons why cyber security can be challenging, organizations can take steps to address these challenges and improve their overall cyber security posture. Whether it's simplifying technology, staying ahead of threats, or addressing human error, there are many ways to improve cyber security. By taking a proactive and informed approach to cyber security, organizations can protect themselves against the latest threats and stay safe in the digital age.
What do you think are the most significant challenges in cyber security? Share your thoughts in the comments below!
