Intro
Boost your ISO 27001 compliance with a comprehensive Statement of Applicability (SOA) template. Discover the 5 essential components to ensure a robust SOA, including scope definition, risk assessment, control selection, and more. Simplify your ISMS implementation with a customizable template that meets ISO 27001 requirements and supports ongoing security monitoring and review.
The ISO 27001 Statement of Applicability (SoA) is a critical document that outlines the controls implemented by an organization to manage information security risks. A well-structured SoA template is essential to ensure compliance with the ISO 27001 standard. In this article, we will discuss the 5 essential components of an ISO 27001 SoA template.
The ISO 27001 SoA is a detailed document that provides an overview of the organization's information security management system (ISMS). It is used to identify, assess, and mitigate information security risks. The SoA template should be comprehensive, yet easy to understand, and should include the following essential components:
1. Scope and Boundaries
The scope and boundaries of the ISMS should be clearly defined in the SoA template. This includes identifying the departments, locations, and systems that are included in the scope of the ISMS. The scope statement should also outline the types of data and information that are protected by the ISMS.
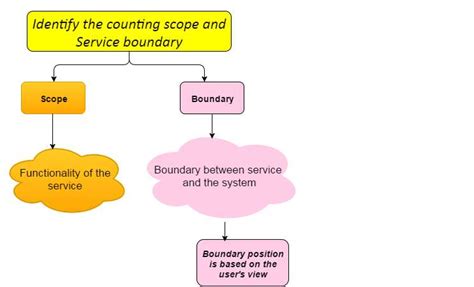
The scope statement should be specific, measurable, achievable, relevant, and time-bound (SMART). It should also be aligned with the organization's overall business objectives.
Key Considerations for Scope and Boundaries:
- Identify the departments, locations, and systems that are included in the scope of the ISMS.
- Define the types of data and information that are protected by the ISMS.
- Ensure that the scope statement is SMART.
2. Risk Assessment and Treatment
The risk assessment and treatment component of the SoA template should outline the organization's approach to identifying, assessing, and mitigating information security risks. This includes identifying the risk assessment methodology, risk criteria, and risk treatment options.
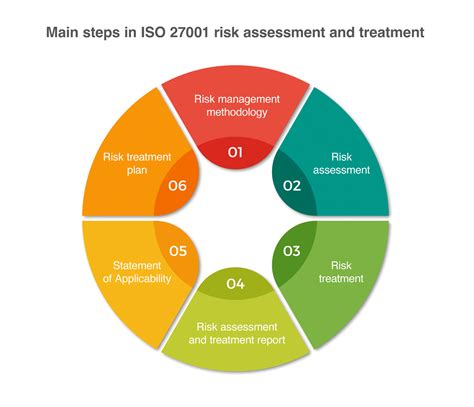
The risk assessment and treatment component should also outline the organization's risk tolerance and risk appetite. This will help to ensure that the organization's risk management approach is aligned with its overall business objectives.
Key Considerations for Risk Assessment and Treatment:
- Identify the risk assessment methodology and risk criteria.
- Outline the risk treatment options, including risk avoidance, risk transfer, and risk mitigation.
- Define the organization's risk tolerance and risk appetite.
3. Control Selection and Implementation
The control selection and implementation component of the SoA template should outline the organization's approach to selecting and implementing controls to manage information security risks. This includes identifying the control objectives, control types, and control implementation.
The control selection and implementation component should also outline the organization's control review and update process. This will help to ensure that the controls remain effective and relevant over time.
Key Considerations for Control Selection and Implementation:
- Identify the control objectives and control types.
- Outline the control implementation approach, including the control owner and control reviewer.
- Define the control review and update process.
4. Monitoring and Review
The monitoring and review component of the SoA template should outline the organization's approach to monitoring and reviewing the ISMS. This includes identifying the monitoring and review methodology, frequency, and scope.

The monitoring and review component should also outline the organization's approach to identifying and addressing ISMS deficiencies and non-conformities.
Key Considerations for Monitoring and Review:
- Identify the monitoring and review methodology, frequency, and scope.
- Outline the approach to identifying and addressing ISMS deficiencies and non-conformities.
- Define the roles and responsibilities for monitoring and review.
5. Continuous Improvement
The continuous improvement component of the SoA template should outline the organization's approach to continually improving the ISMS. This includes identifying the continuous improvement methodology, objectives, and scope.
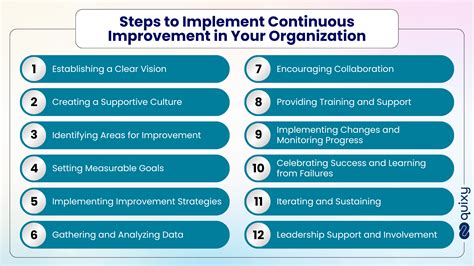
The continuous improvement component should also outline the organization's approach to identifying and addressing ISMS opportunities for improvement.
Key Considerations for Continuous Improvement:
- Identify the continuous improvement methodology, objectives, and scope.
- Outline the approach to identifying and addressing ISMS opportunities for improvement.
- Define the roles and responsibilities for continuous improvement.
ISO 27001 SoA Template Image Gallery
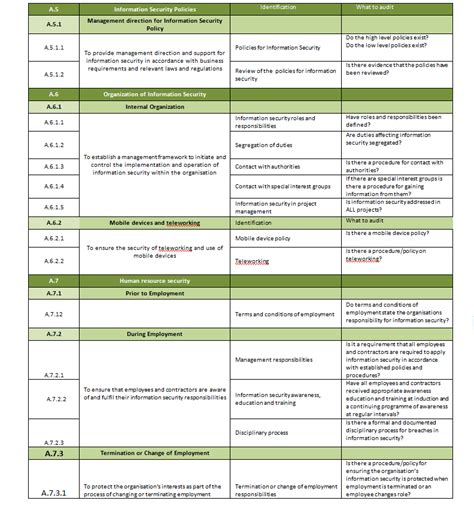
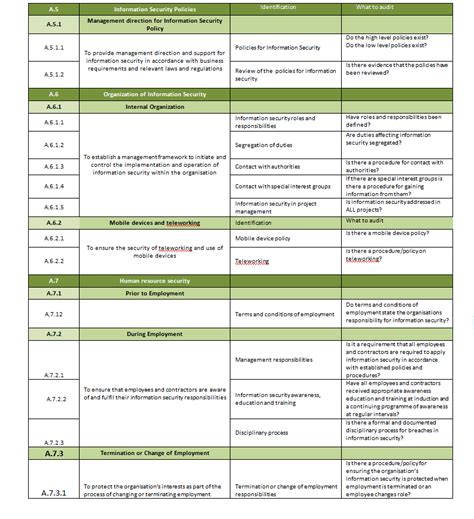
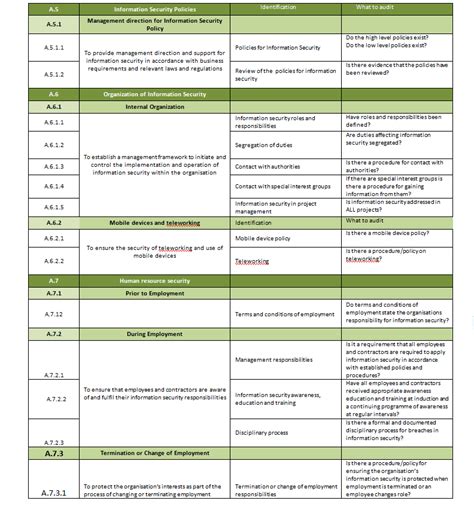
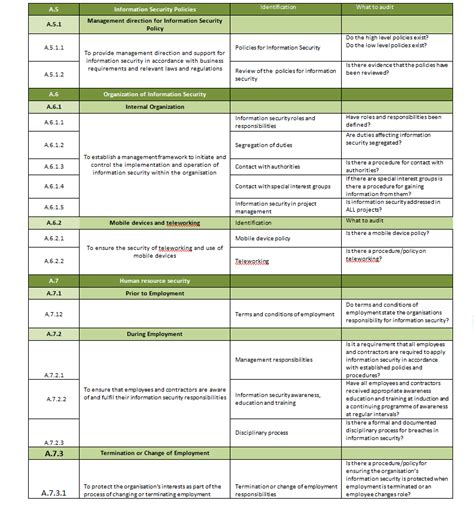
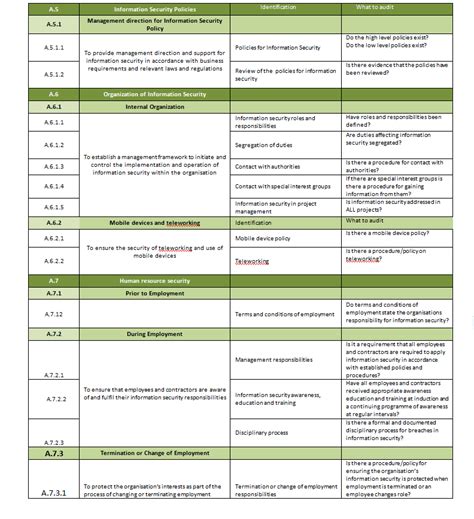
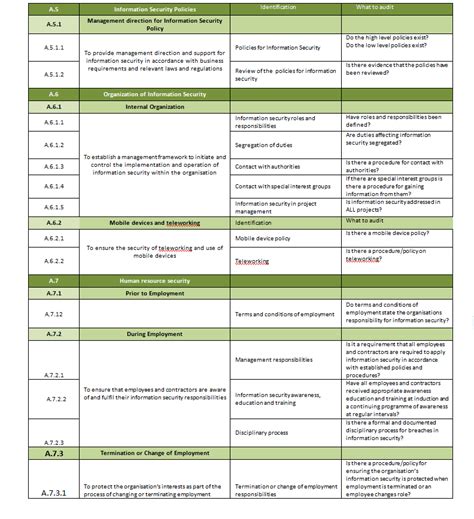
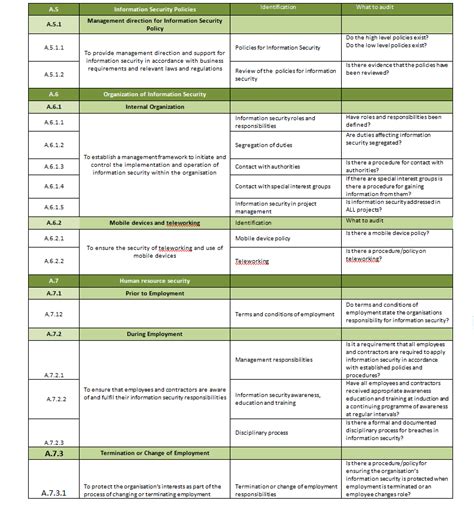
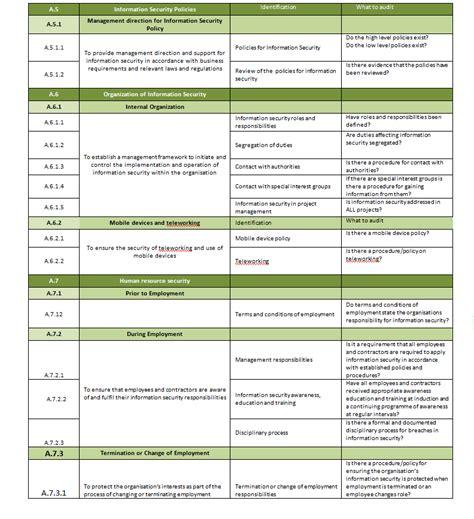
In conclusion, an ISO 27001 SoA template is an essential document that outlines the controls implemented by an organization to manage information security risks. The 5 essential components of an ISO 27001 SoA template include scope and boundaries, risk assessment and treatment, control selection and implementation, monitoring and review, and continuous improvement. By following these components, organizations can ensure that their ISMS is effective and compliant with the ISO 27001 standard.
We hope that this article has provided you with valuable insights into the essential components of an ISO 27001 SoA template. If you have any questions or comments, please feel free to share them with us.
