Intro
Streamline your network setup with router configuration letter templates. Discover expert-approved templates and learn how to configure routers for optimal network performance. Master subnet masking, IP addressing, and port forwarding with ease. Download customizable templates and take your network administration skills to the next level.
Router configuration is a crucial task for network administrators, as it enables them to manage and secure their networks effectively. A well-configured router can help prevent unauthorized access, ensure data integrity, and optimize network performance. However, configuring a router can be a complex task, especially for those who are new to network administration.
In this article, we will provide router configuration letter templates that network administrators can use as a guide to configure their routers. We will also discuss the importance of router configuration, the benefits of using templates, and the key elements that should be included in a router configuration template.
Why is Router Configuration Important?
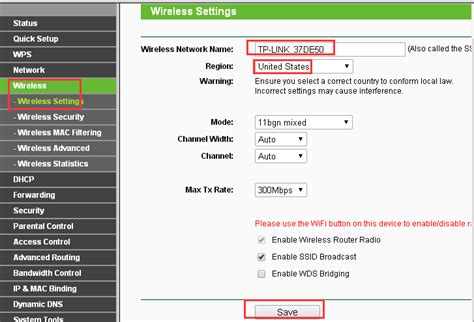
Router configuration is important for several reasons:
- Network Security: A well-configured router can help prevent unauthorized access to the network, reducing the risk of cyber attacks and data breaches.
- Network Performance: A properly configured router can optimize network performance, ensuring that data is transmitted efficiently and effectively.
- Data Integrity: A configured router can help ensure data integrity, preventing data corruption and loss.
- Compliance: Router configuration can help organizations comply with regulatory requirements, such as PCI DSS and HIPAA.
Benefits of Using Router Configuration Templates

Using router configuration templates can provide several benefits, including:
- Time Savings: Templates can save time and effort, as network administrators do not have to start from scratch when configuring a router.
- Consistency: Templates can ensure consistency in router configuration, reducing the risk of errors and inconsistencies.
- Standardization: Templates can help standardize router configuration, making it easier to manage and maintain networks.
- Compliance: Templates can help organizations comply with regulatory requirements, reducing the risk of non-compliance.
Key Elements of a Router Configuration Template

A router configuration template should include the following key elements:
- Router Information: This includes the router's IP address, subnet mask, and default gateway.
- Network Information: This includes the network's IP address range, subnet mask, and VLAN information.
- Security Settings: This includes firewall rules, access control lists, and authentication settings.
- Quality of Service (QoS) Settings: This includes settings for traffic prioritization and bandwidth allocation.
- Monitoring and Logging Settings: This includes settings for logging, monitoring, and alerting.
Router Configuration Letter Templates

Here are some router configuration letter templates that network administrators can use:
Template 1: Basic Router Configuration
[Router IP Address] [Subnet Mask] [Default Gateway]
Template 2: Advanced Router Configuration
[Router IP Address] [Subnet Mask] [Default Gateway] [Firewall Rules] [Access Control Lists] [Authentication Settings]
Template 3: QoS Configuration
[Router IP Address] [Subnet Mask] [Default Gateway] [Traffic Prioritization Settings] [Bandwidth Allocation Settings]
Template 4: Monitoring and Logging Configuration
[Router IP Address] [Subnet Mask] [Default Gateway] [Logging Settings] [Monitoring Settings] [Alerting Settings]
Best Practices for Router Configuration
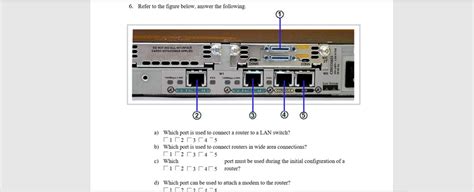
Here are some best practices for router configuration:
- Use Strong Passwords: Use strong passwords for router access and authentication.
- Use Encryption: Use encryption for data transmission and storage.
- Use Firewalls: Use firewalls to block unauthorized access to the network.
- Use Access Control Lists: Use access control lists to restrict access to the network.
- Use Monitoring and Logging: Use monitoring and logging to detect and respond to security incidents.
Router Configuration Image Gallery







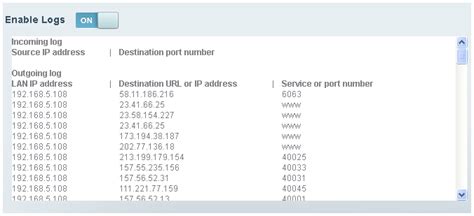
We hope this article has provided you with a comprehensive guide to router configuration, including templates and best practices. By following these guidelines, you can ensure that your router is configured correctly and securely, and that your network is protected from unauthorized access and cyber threats.
If you have any questions or comments about this article, please leave a comment below. We would love to hear from you!
