Intro
Accelerate NIST 800-171 compliance with 5 essential policy templates. Simplify your security framework with pre-built templates for Access Control, Incident Response, and more. Streamline audit preparation and ensure DFARS compliance. Download customizable templates to strengthen your cybersecurity posture and protect Controlled Unclassified Information (CUI).
As organizations strive to protect their sensitive information and comply with regulatory requirements, the need for robust security policies and procedures has become increasingly important. One such regulation is NIST 800-171, which provides guidelines for protecting Controlled Unclassified Information (CUI) in non-federal information systems and organizations. In this article, we will discuss the essential NIST 800-171 policy templates that organizations can use to ensure compliance and enhance their overall security posture.
The importance of NIST 800-171 compliance cannot be overstated. Non-compliance can result in severe consequences, including loss of contracts, reputational damage, and financial penalties. Furthermore, the increasing sophistication of cyber threats demands that organizations prioritize the protection of their sensitive information. By implementing effective security policies and procedures, organizations can minimize the risk of data breaches and ensure the confidentiality, integrity, and availability of their sensitive information.
NIST 800-171 provides a comprehensive framework for protecting CUI, and its requirements are divided into 14 control families. These control families include Access Control, Awareness and Training, Audit and Accountability, Configuration Management, Identification and Authentication, Incident Response, Maintenance, Media Protection, Personnel Security, Physical Protection, Risk Assessment, Security Assessment, System and Communications Protection, and System and Information Integrity.
1. Access Control Policy Template

An Access Control policy template is essential for ensuring that only authorized personnel have access to sensitive information. This template should include procedures for user account management, access control lists, and separation of duties. By implementing an Access Control policy, organizations can prevent unauthorized access to sensitive information and minimize the risk of data breaches.
The Access Control policy template should include the following elements:
- User account management procedures
- Access control list procedures
- Separation of duties procedures
- Access control enforcement procedures
Example of Access Control Policy Template
"All users must be authenticated before accessing sensitive information. Access control lists will be used to restrict access to sensitive information based on user roles. Separation of duties will be implemented to prevent any single individual from having too much access to sensitive information."
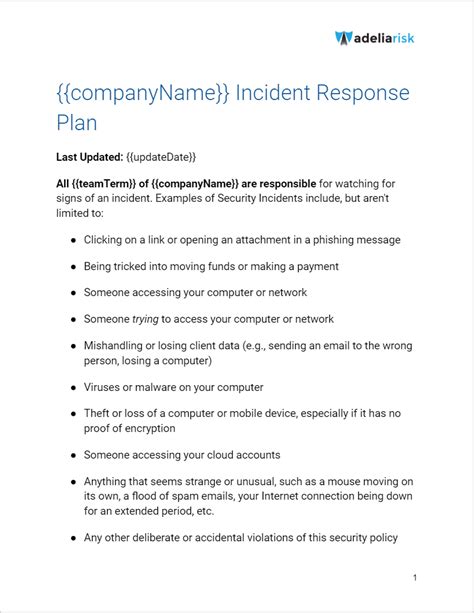
2. Incident Response Policy Template
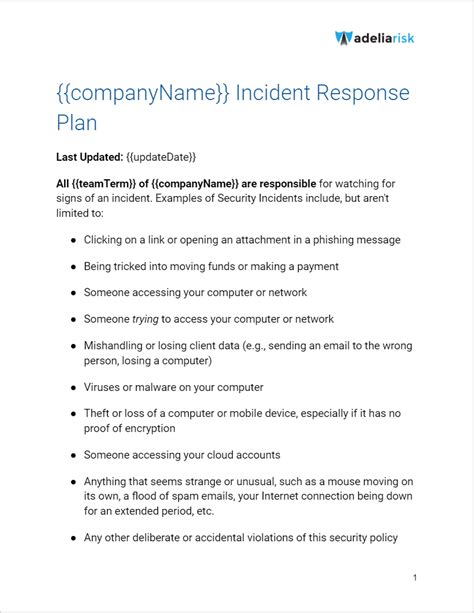
An Incident Response policy template is crucial for ensuring that organizations are prepared to respond to security incidents in a timely and effective manner. This template should include procedures for incident detection, reporting, and response. By implementing an Incident Response policy, organizations can minimize the impact of security incidents and prevent data breaches.
The Incident Response policy template should include the following elements:
- Incident detection procedures
- Incident reporting procedures
- Incident response procedures
- Incident containment procedures
Example of Incident Response Policy Template
"All security incidents must be reported to the incident response team immediately. The incident response team will assess the incident and respond accordingly. Incident containment procedures will be implemented to prevent further damage."
3. Risk Assessment Policy Template
A Risk Assessment policy template is essential for identifying and mitigating risks to sensitive information. This template should include procedures for risk assessment, risk mitigation, and risk monitoring. By implementing a Risk Assessment policy, organizations can identify potential risks and take proactive measures to mitigate them.
The Risk Assessment policy template should include the following elements:
- Risk assessment procedures
- Risk mitigation procedures
- Risk monitoring procedures
- Risk review procedures
Example of Risk Assessment Policy Template
"All risks to sensitive information must be assessed and mitigated. Risk assessments will be conducted annually, and risk mitigation procedures will be implemented accordingly. Risk monitoring will be conducted quarterly to ensure that risks are being mitigated effectively."
4. Security Awareness and Training Policy Template

A Security Awareness and Training policy template is crucial for ensuring that employees are aware of security best practices and procedures. This template should include procedures for security awareness and training, as well as procedures for security awareness and training programs. By implementing a Security Awareness and Training policy, organizations can educate employees on security best practices and procedures.
The Security Awareness and Training policy template should include the following elements:
- Security awareness procedures
- Security training procedures
- Security awareness and training programs
- Security awareness and training evaluation procedures
Example of Security Awareness and Training Policy Template
"All employees must participate in security awareness and training programs annually. Security awareness and training programs will be conducted quarterly, and security awareness and training evaluation procedures will be implemented to ensure that employees are aware of security best practices and procedures."
5. Configuration Management Policy Template

A Configuration Management policy template is essential for ensuring that all changes to systems and applications are properly managed and documented. This template should include procedures for configuration management, change control, and configuration monitoring. By implementing a Configuration Management policy, organizations can ensure that all changes to systems and applications are properly managed and documented.
The Configuration Management policy template should include the following elements:
- Configuration management procedures
- Change control procedures
- Configuration monitoring procedures
- Configuration review procedures
Example of Configuration Management Policy Template
"All changes to systems and applications must be properly managed and documented. Change control procedures will be implemented to ensure that all changes are approved and documented. Configuration monitoring will be conducted quarterly to ensure that all changes are properly managed and documented."
NIST 800-171 Policy Templates Gallery







In conclusion, implementing NIST 800-171 policy templates is essential for ensuring compliance with regulatory requirements and enhancing overall security posture. By using these policy templates, organizations can ensure that they are protecting sensitive information effectively and minimizing the risk of data breaches. We encourage you to share your thoughts and experiences with implementing NIST 800-171 policy templates in the comments section below.
