Intro
Streamline your NIST 800-171 compliance process with our expert guide. Learn how to complete the NIST 800-171 SSP template in 7 straightforward steps. Master the requirements, assessment, and implementation of the Security Requirements Guide (SRG) and System Security Plan (SSP) with ease. Boost your cybersecurity posture and avoid costly delays.
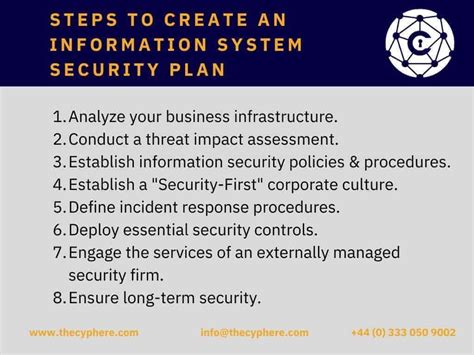
Implementing the National Institute of Standards and Technology (NIST) Special Publication 800-171 (SP 800-171) is a crucial step for organizations that handle Controlled Unclassified Information (CUI) to ensure the security and integrity of sensitive data. The NIST 800-171 System Security Plan (SSP) template is a valuable tool to help organizations develop a comprehensive security plan. Here's a 7-step guide to complete the NIST 800-171 SSP template:
Understanding the NIST 800-171 SSP Template
Before diving into the steps, it's essential to understand the purpose and structure of the NIST 800-171 SSP template. The template is designed to help organizations create a System Security Plan (SSP) that outlines the security controls and procedures for protecting CUI.
Benefits of Completing the NIST 800-171 SSP Template
- Ensures compliance with NIST 800-171 requirements
- Provides a comprehensive security plan for protecting CUI
- Helps organizations identify and mitigate security risks
- Enhances the overall security posture of the organization
Step 1: Identify the Scope of the SSP
The first step is to identify the scope of the SSP, including the systems, networks, and personnel that will be covered by the plan. This includes:
- Identifying the systems and networks that handle CUI
- Determining the personnel who will be responsible for implementing and maintaining the SSP
- Establishing the boundaries of the SSP, including any third-party providers or contractors
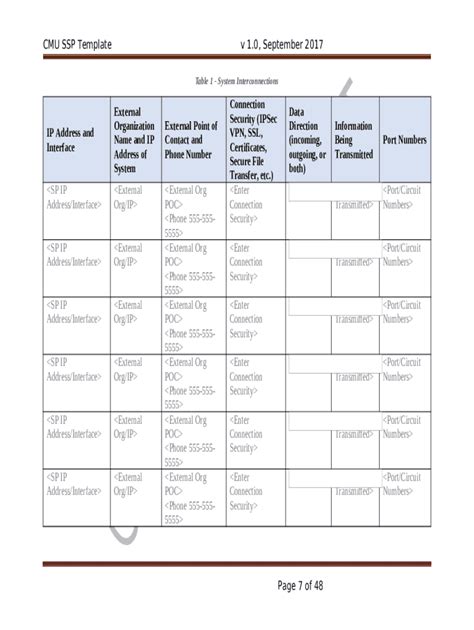
Scope of SSP Template Sections
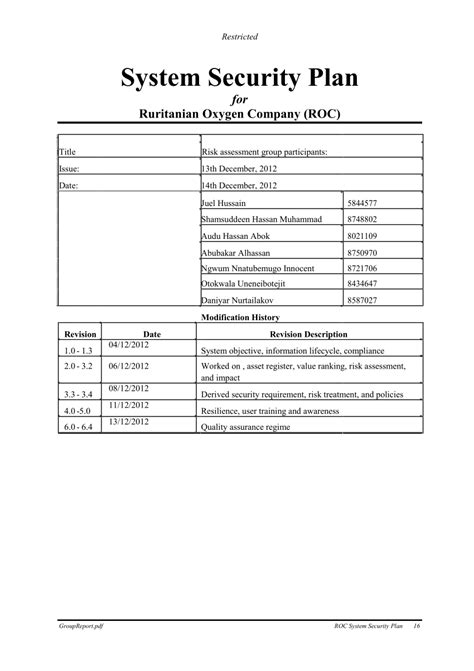
- Section 1: System Identification
- Section 2: System Description
- Section 3: System Boundaries
Step 2: Conduct a Risk Assessment

The second step is to conduct a risk assessment to identify potential security risks to the systems and networks that handle CUI. This includes:
- Identifying potential threats and vulnerabilities
- Assessing the likelihood and impact of potential risks
- Prioritizing risks based on their severity and likelihood
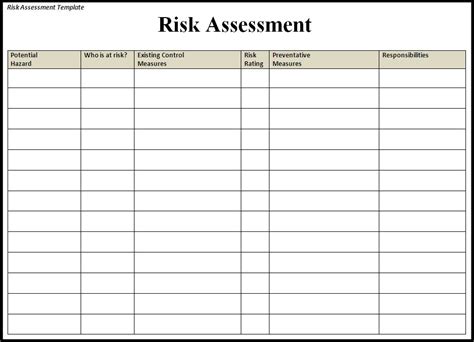
Risk Assessment Template Sections
- Section 4: Risk Assessment
- Section 5: Risk Mitigation
Step 3: Develop Security Controls

The third step is to develop security controls to mitigate the identified risks. This includes:
- Implementing security controls to protect CUI
- Developing procedures for incident response and disaster recovery
- Establishing security awareness training for personnel
Security Controls Template Sections
- Section 6: Security Controls
- Section 7: Incident Response
- Section 8: Disaster Recovery
Step 4: Implement Security Measures
The fourth step is to implement security measures to protect CUI. This includes:
- Implementing access controls, including authentication and authorization
- Establishing encryption and key management procedures
- Implementing network security measures, including firewalls and intrusion detection
Security Measures Template Sections
- Section 9: Access Control
- Section 10: Encryption and Key Management
- Section 11: Network Security
Step 5: Conduct Continuous Monitoring

The fifth step is to conduct continuous monitoring to ensure the effectiveness of the SSP. This includes:
- Monitoring system logs and network traffic
- Conducting regular security audits and risk assessments
- Implementing incident response and disaster recovery procedures
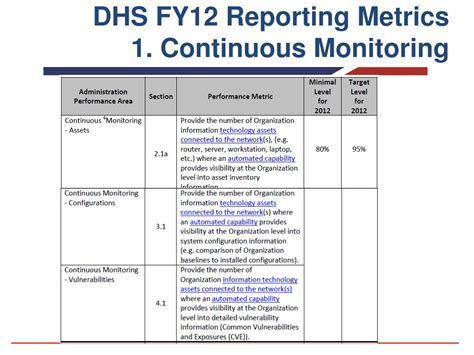
Continuous Monitoring Template Sections
- Section 12: Continuous Monitoring
- Section 13: Security Audits
- Section 14: Incident Response and Disaster Recovery
Step 6: Review and Update the SSP

The sixth step is to review and update the SSP regularly to ensure it remains effective and compliant with NIST 800-171 requirements. This includes:
- Reviewing the SSP annually or as needed
- Updating the SSP to reflect changes to the system or network
- Ensuring the SSP remains compliant with NIST 800-171 requirements
Review and Update SSP Template Sections
- Section 15: Review and Update SSP
Step 7: Obtain Approval and Certification

The seventh and final step is to obtain approval and certification for the SSP. This includes:
- Obtaining approval from the designated approving authority
- Obtaining certification from a third-party auditor or certifying body
- Ensuring the SSP is compliant with NIST 800-171 requirements
Approval and Certification Template Sections
- Section 16: Approval and Certification
NIST 800-171 SSP Template Image Gallery


By following these 7 steps, organizations can complete the NIST 800-171 SSP template and ensure compliance with NIST 800-171 requirements. Remember to review and update the SSP regularly to ensure it remains effective and compliant.
We hope this article has provided valuable insights into completing the NIST 800-171 SSP template. If you have any questions or need further clarification, please don't hesitate to ask. Share your experiences and thoughts on completing the NIST 800-171 SSP template in the comments below.
