Intro
Boost your risk management strategy with the NIST 800-30 template. Learn how to implement this framework in 5 effective ways, covering risk assessment, mitigation, and monitoring. Discover how to identify, analyze, and prioritize risks, and ensure compliance with NIST guidelines, enhancing your organizations security posture and reducing vulnerabilities.
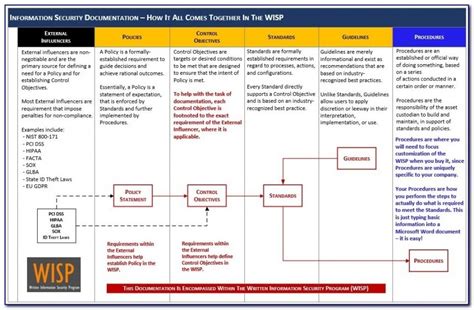
The National Institute of Standards and Technology (NIST) Special Publication 800-30, "Guide for Conducting Risk Assessments," provides a comprehensive framework for identifying, assessing, and mitigating risks to organizational operations and assets. The NIST 800-30 template is a widely accepted tool for conducting risk assessments, and implementing it can help organizations improve their risk management practices. Here are five ways to implement the NIST 800-30 template:
Understanding the NIST 800-30 Template
Before implementing the NIST 800-30 template, it is essential to understand its structure and components. The template consists of nine steps, which are divided into three phases: risk assessment preparation, risk assessment, and risk assessment reporting.
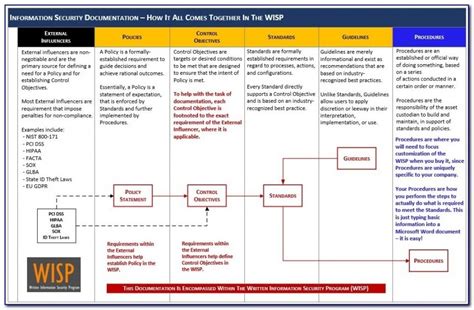
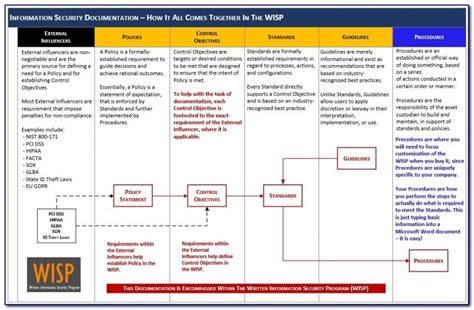
Phase 1: Risk Assessment Preparation
Step 1: Define the Scope of the Risk Assessment
The first step in implementing the NIST 800-30 template is to define the scope of the risk assessment. This involves identifying the organizational assets, data, and systems that need to be assessed.
Identify the Risk Assessment Team
Assemble a team of stakeholders, including IT staff, security experts, and business representatives, to participate in the risk assessment process.
Establish the Risk Assessment Criteria
Establish the criteria for evaluating and prioritizing risks, such as the likelihood and potential impact of a security breach.
Phase 2: Risk Assessment
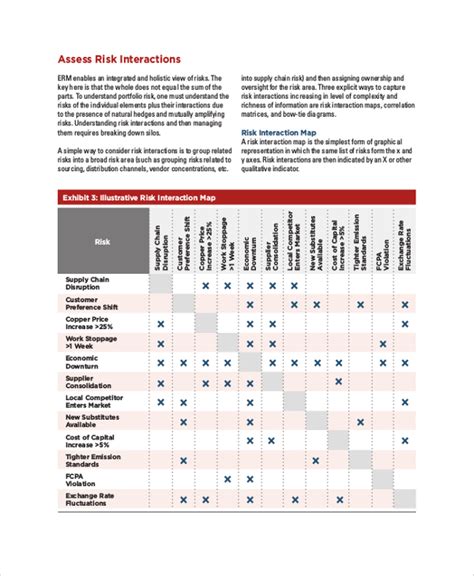
Step 2: Identify Threats and Vulnerabilities
Identify potential threats and vulnerabilities to the organizational assets, data, and systems.

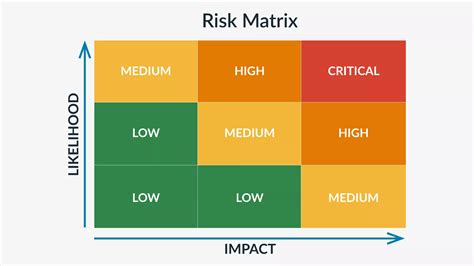
Assess the Likelihood and Potential Impact of Threats
Assess the likelihood and potential impact of each threat and vulnerability, using a risk assessment matrix or other tools.
Identify Controls and Countermeasures
Identify existing controls and countermeasures that can mitigate the risks, such as firewalls, intrusion detection systems, and access controls.
Phase 3: Risk Assessment Reporting
Step 3: Develop a Risk Assessment Report
Develop a comprehensive risk assessment report that summarizes the findings and recommendations for mitigating the risks.
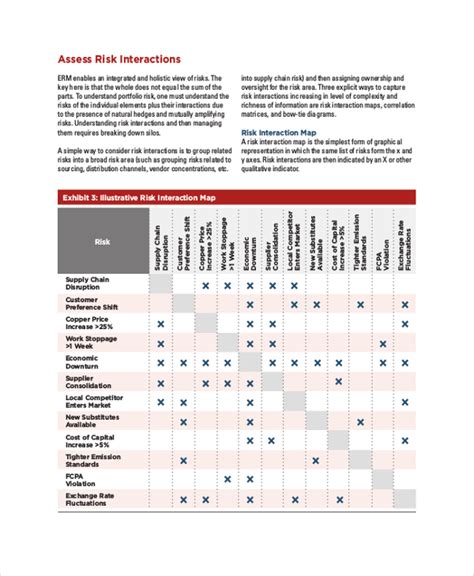
Present the Risk Assessment Report to Stakeholders
Present the risk assessment report to stakeholders, including senior management, IT staff, and security experts.
Implement Risk Mitigation Measures
Implement risk mitigation measures, such as patching vulnerabilities, implementing new controls, and providing training to employees.
Gallery of NIST 800-30 Template Implementation
NIST 800-30 Template Implementation Gallery
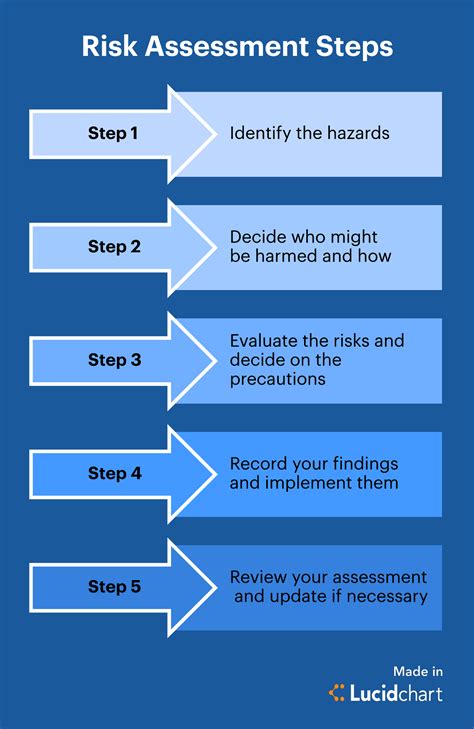



By following these five ways to implement the NIST 800-30 template, organizations can improve their risk management practices, reduce the likelihood of security breaches, and protect their assets and data.
We hope this article has provided valuable insights into implementing the NIST 800-30 template. If you have any questions or comments, please feel free to share them below.
