Intro
Unlock the mysteries of military codes with numbers as the key. Discover how numerical patterns and cryptographic techniques are used to decode classified information. Learn about the role of math in military intelligence, from cipher systems to encoded messages, and explore the fascinating world of numerical code-breaking.
In the realm of military secrets, numbers have long been a crucial component in code-making and code-breaking. From ancient civilizations to modern-day warfare, the power of numbers has played a significant role in the art of cryptography. In this article, we will delve into the world of numerical codes, exploring their history, mechanics, and significance in the military.
The Early Days of Numerical Codes
The use of numbers in codes dates back to ancient times, with examples found in Egyptian hieroglyphics, Greek cryptography, and Roman ciphers. One of the earliest known numerical codes was the Caesar Cipher, used by Julius Caesar to communicate with his generals. This simple substitution cipher replaced each letter with a letter a fixed number of positions down the alphabet.
Substitution and Transposition Ciphers
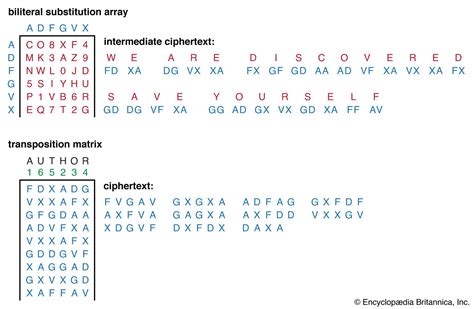
In the Middle Ages, numerical codes evolved with the development of substitution and transposition ciphers. Substitution ciphers replaced each letter with a different letter or symbol, while transposition ciphers rearranged the letters according to a specific pattern. The Vigenère cipher, a polyalphabetic substitution cipher, was considered unbreakable for centuries.
The Rise of Mathematical Cryptography
The 20th century saw a significant shift in cryptography with the advent of mathematical cryptography. The invention of the Enigma machine by German engineer Arthur Scherbius in the 1920s revolutionized code-making. The machine used a complex system of rotors and substitution tables to encrypt messages.
Code-Breaking and the Role of Numbers
Code-breaking, the process of deciphering encrypted messages, relies heavily on numbers. The famous cryptanalyst, William Friedman, used statistical analysis and frequency counts to crack the Japanese Purple cipher during World War II. The British Government Code and Cypher School (GC&CS) at Bletchley Park also employed numerical methods to break the Enigma code.
The Computer Age and Public-Key Cryptography

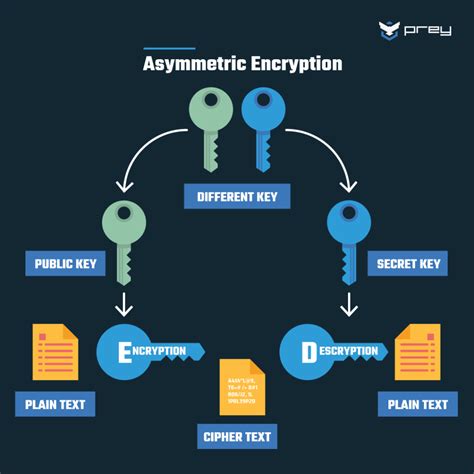
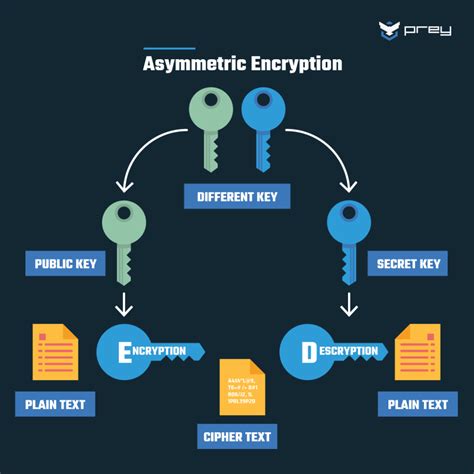
The advent of computers and public-key cryptography in the 1970s transformed the field of cryptography. Public-key cryptography uses numerical keys, comprising large prime numbers, to encrypt and decrypt messages. This method ensures secure communication over the internet, with popular algorithms like RSA and elliptic curve cryptography.
Numerical Challenges in Modern Cryptography
Despite advancements in cryptography, numerical challenges persist. Factorization, the process of breaking down large composite numbers into their prime factors, remains a significant challenge. The security of many cryptographic protocols relies on the difficulty of factorization, making it an active area of research.
Cryptography in Modern Warfare

Cryptography plays a vital role in modern warfare, with military organizations relying on secure communication networks to coordinate operations. Advanced cryptographic techniques, such as quantum cryptography, are being explored to address emerging threats.
The Future of Numerical Codes
As technology advances, the power of numbers in code-making and code-breaking will continue to evolve. Researchers are exploring new areas, such as quantum computing and machine learning, to develop more secure and efficient cryptographic methods.
Conclusion and Future Directions
The power of numbers in codes has come a long way, from ancient civilizations to modern-day warfare. As cryptography continues to evolve, it is essential to understand the significance of numerical codes in ensuring secure communication. As we move forward, researchers and cryptanalysts must stay ahead of emerging threats, harnessing the power of numbers to develop more robust and secure cryptographic methods.
Numerical Codes Image Gallery