Identify hidden threats in your organization with our expert guide. Learn 7 ways to spot a part contributor whos an infiltrator, including behaviors, communication patterns, and work habits. Discover how to detect and prevent sabotage, data breaches, and intellectual property theft, ensuring a secure and productive work environment.
In today's world, identifying individuals who may be infiltrating a group or organization with ulterior motives is more crucial than ever. Whether it's a contributor to a community, a team member in a company, or a volunteer for a cause, recognizing potential infiltrators can help prevent harm and maintain trust. In this article, we'll explore seven ways to spot a part contributor who may be an infiltrator.
Understanding the Importance of Trust and Vigilance
In any group or organization, trust is a fundamental component that allows members to work together effectively and achieve common goals. However, this trust can be easily broken when an infiltrator is introduced into the mix. Infiltrators may have hidden agendas, such as gathering information, sabotaging efforts, or causing harm to the group or its members.
It's essential to remain vigilant and take proactive steps to identify potential infiltrators before they can cause damage. By recognizing the signs and taking action, you can protect your group and maintain the trust that's so crucial to its success.
Seven Ways to Spot a Part Contributor Who's an Infiltrator
1. Inconsistent Behavior and Incongruent Messages
Infiltrators often struggle to maintain a consistent image or message, as their true intentions may not align with those of the group. Look for individuals who frequently contradict themselves, change their story, or fail to follow through on commitments.
- Be wary of contributors who:
- Frequently change their narrative or backpedal on previous statements.
- Use manipulative language or gaslighting tactics to control conversations.
- Display inconsistent behavior, such as being overly friendly one day and hostile the next.
2. Overly Aggressive or Invasive Questioning
Infiltrators may use questioning as a means to gather information or cause tension within the group. Be cautious of individuals who:
- Ask invasive or prying questions that seem unrelated to the topic at hand.
- Display an unusual level of interest in sensitive or confidential information.
- Use aggressive or confrontational language when questioning others.

3. Unusual or Unexplained Behavior
Infiltrators may exhibit behavior that seems unusual or unexplained, such as:
- Displaying an unnatural level of curiosity or interest in specific topics.
- Engaging in behaviors that seem out of character or inconsistent with their stated goals.
- Being overly secretive or evasive when questioned about their actions or intentions.
4. Lack of Transparency or Accountability
Infiltrators often struggle with transparency and accountability, as their true intentions may not align with those of the group. Be wary of contributors who:
- Fail to disclose relevant information or hide behind anonymity.
- Display a lack of accountability for their actions or decisions.
- Become defensive or hostile when questioned about their behavior.
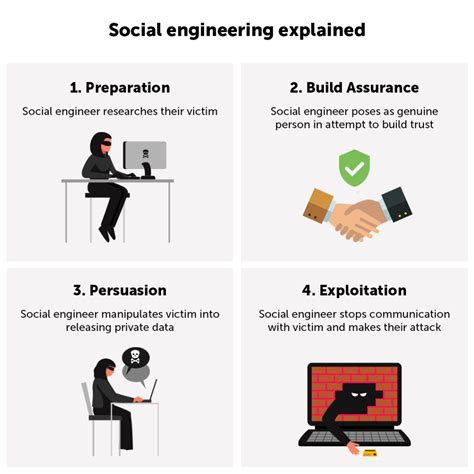
5. Infiltration through Social Engineering
Infiltrators may use social engineering tactics to gain the trust of group members and gain access to sensitive information. Be cautious of individuals who:
- Use charm or manipulation to build relationships or gain influence.
- Display an unusual level of interest in personal or sensitive information.
- Use psychological manipulation to control or influence others.
6. Unusual Patterns of Behavior
Infiltrators may exhibit patterns of behavior that seem unusual or suspicious, such as:
- Displaying an unnatural level of interest in specific topics or individuals.
- Engaging in behaviors that seem out of character or inconsistent with their stated goals.
- Being overly secretive or evasive when questioned about their actions or intentions.
7. Verification of Credentials and Background
Finally, it's essential to verify the credentials and background of any contributor, especially if they're new to the group. Be wary of individuals who:
- Fail to provide clear or consistent information about their background or credentials.
- Display a lack of transparency about their intentions or goals.
- Become defensive or hostile when questioned about their credentials or background.
Gallery of Infiltration Tactics
Infiltration Tactics Image Gallery






Take Action and Protect Your Group
Identifying potential infiltrators is just the first step. Once you've recognized the signs, it's essential to take action to protect your group and maintain trust. Here are some steps you can take:
- Verify the credentials and background of new contributors.
- Set clear boundaries and expectations for behavior.
- Encourage transparency and accountability within the group.
- Be cautious of individuals who display unusual or suspicious behavior.
- Take action quickly if you suspect an infiltrator is present in your group.
By being vigilant and taking proactive steps, you can protect your group and maintain the trust that's so crucial to its success.
Engage with the Community and Share Your Thoughts
We'd love to hear from you! Share your thoughts and experiences with identifying and dealing with infiltrators in the comments below. Have you encountered an infiltrator in a group or organization? How did you handle the situation? Let's work together to build trust and maintain the integrity of our communities.
