Intro
Enhance healthcare security with a robust Security Operations Center (SOC). Learn how a SOC for health scientists protects sensitive data, detects threats, and ensures HIPAA compliance. Discover the benefits of a dedicated SOC in healthcare, including threat intelligence, incident response, and continuous monitoring.
In today's digital age, the healthcare industry is heavily reliant on technology to manage patient data, medical records, and other sensitive information. However, this increased dependence on technology also makes healthcare organizations more vulnerable to cyber threats and data breaches. To mitigate these risks, a Security Operations Center (SOC) is essential for health scientists to ensure the confidentiality, integrity, and availability of sensitive data.
The importance of a SOC for health scientists cannot be overstated. A SOC is a centralized unit that monitors and analyzes an organization's security-related data to identify potential security threats and incidents. It provides real-time threat detection, incident response, and remediation, allowing health scientists to focus on their core responsibilities without worrying about the security of their data. In this article, we will explore the benefits of a SOC for health scientists, its working mechanisms, and the steps to implement a SOC.
Benefits of a Security Operations Center for Health Scientists

A SOC provides numerous benefits to health scientists, including:
- Real-time threat detection: A SOC uses advanced threat detection tools to identify potential security threats in real-time, allowing health scientists to respond quickly and minimize the impact of a breach.
- Improved incident response: A SOC provides a structured approach to incident response, ensuring that health scientists can respond to security incidents quickly and effectively.
- Enhanced security posture: A SOC helps health scientists to identify vulnerabilities in their systems and take corrective action to strengthen their security posture.
- Compliance with regulations: A SOC helps health scientists to comply with relevant regulations, such as HIPAA, by ensuring that sensitive data is properly protected.
- Reduced costs: A SOC can help health scientists to reduce costs by minimizing the impact of security breaches and reducing the need for costly remediation efforts.
Working Mechanisms of a Security Operations Center
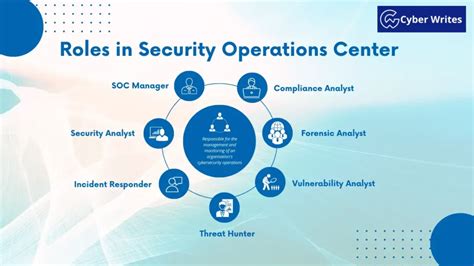
A SOC typically consists of several key components, including:
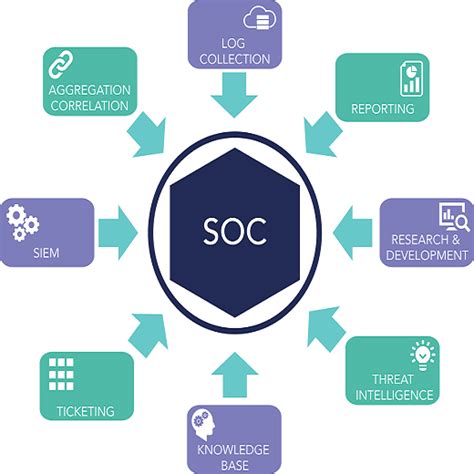
- Security Information and Event Management (SIEM) system: A SIEM system collects and analyzes security-related data from various sources to identify potential security threats.
- Threat intelligence: Threat intelligence involves gathering and analyzing data on potential security threats to identify trends and patterns.
- Incident response: Incident response involves responding to security incidents quickly and effectively to minimize the impact of a breach.
- Security orchestration, automation, and response (SOAR): SOAR involves automating security incident response processes to improve efficiency and effectiveness.
Steps to Implement a Security Operations Center
Implementing a SOC requires careful planning and execution. Here are the steps to follow:
- Define the scope and objectives: Define the scope and objectives of the SOC, including the types of security threats to be monitored and the incident response processes to be followed.
- Select the right technology: Select the right technology, including a SIEM system, threat intelligence tools, and SOAR solutions, to support the SOC.
- Build a skilled team: Build a skilled team of security professionals, including analysts, incident responders, and threat hunters, to staff the SOC.
- Develop incident response processes: Develop incident response processes and procedures to ensure that security incidents are responded to quickly and effectively.
- Continuously monitor and improve: Continuously monitor and improve the SOC, including the technology, processes, and team, to ensure that it remains effective and efficient.
Best Practices for a Security Operations Center
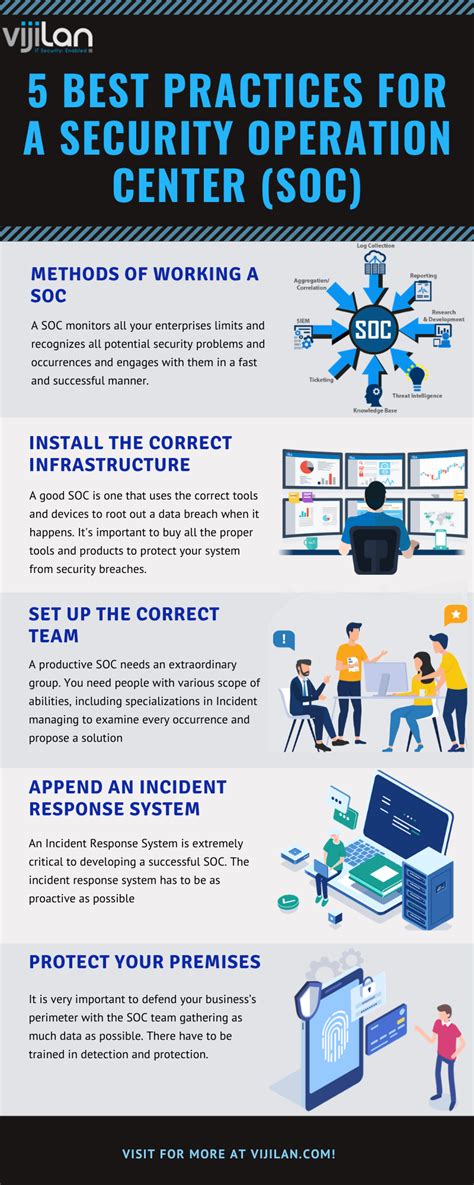
Here are some best practices for a SOC:
- Use a structured approach: Use a structured approach to incident response, including incident classification, escalation, and resolution.
- Continuously monitor and analyze: Continuously monitor and analyze security-related data to identify potential security threats.
- Use threat intelligence: Use threat intelligence to gather and analyze data on potential security threats.
- Use automation and orchestration: Use automation and orchestration to improve efficiency and effectiveness.
- Continuously train and educate: Continuously train and educate the SOC team to ensure that they have the skills and knowledge needed to respond to security incidents effectively.
Common Challenges and Solutions

Here are some common challenges and solutions for a SOC:
- Challenge: Lack of skilled personnel: Solution: Provide training and education to the SOC team to ensure that they have the skills and knowledge needed to respond to security incidents effectively.
- Challenge: Inadequate technology: Solution: Select the right technology, including a SIEM system, threat intelligence tools, and SOAR solutions, to support the SOC.
- Challenge: Inadequate processes: Solution: Develop incident response processes and procedures to ensure that security incidents are responded to quickly and effectively.
Future of Security Operations Centers

The future of SOCs is likely to involve increased use of artificial intelligence (AI) and machine learning (ML) to improve incident response and threat detection. Additionally, SOCs will need to adapt to emerging technologies, such as cloud computing and the Internet of Things (IoT).
Conclusion
A SOC is essential for health scientists to ensure the confidentiality, integrity, and availability of sensitive data. By understanding the benefits, working mechanisms, and steps to implement a SOC, health scientists can improve their security posture and reduce the risk of security breaches.
Gallery of Security Operations Center for Health Scientists
Security Operations Center for Health Scientists Image Gallery










We hope this article has provided valuable insights into the importance of a SOC for health scientists. If you have any questions or comments, please feel free to share them below.
