Intro
Boost your online security with expert advice from Steve Proud. Discover 5 ways to fortify your cybersecurity defenses, including threat detection, incident response, and proactive measures to prevent cyber attacks. Learn how to protect your digital assets and stay ahead of cyber threats with these actionable tips and strategies.
In today's digital age, cybersecurity has become a top priority for businesses and individuals alike. With the rise of technology and the internet, the risk of cyber threats has increased exponentially, making it essential to take proactive measures to protect oneself from these threats. Steve Proud, a renowned cybersecurity expert, has been at the forefront of this effort, providing valuable insights and strategies to help individuals and organizations shore up their cybersecurity. In this article, we will explore five ways Steve Proud helps to strengthen cybersecurity.
Understanding the Threat Landscape
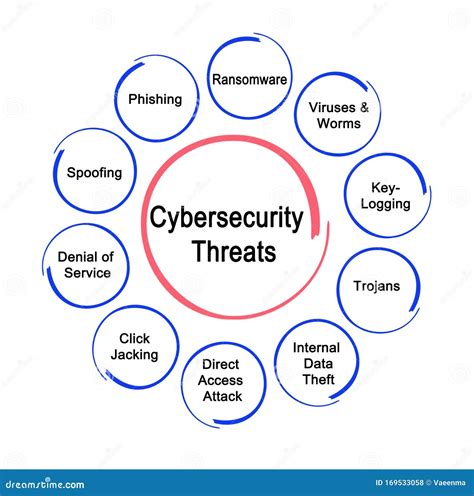
Before we dive into the ways Steve Proud enhances cybersecurity, it's essential to understand the threat landscape. Cyber threats are becoming increasingly sophisticated, with hackers using various tactics to breach security systems. These threats can come in the form of phishing emails, malware, ransomware, and even social engineering attacks. Steve Proud emphasizes the importance of staying informed about these threats and understanding how they can impact individuals and organizations.
5 Ways Steve Proud Shores Up Cybersecurity
1. Implementing a Layered Security Approach
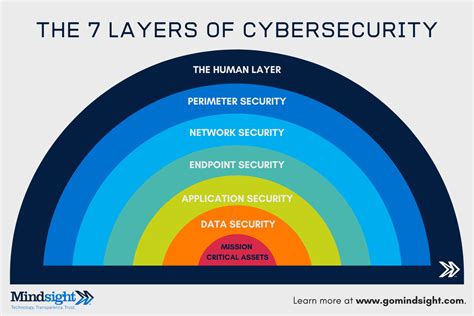
Steve Proud advocates for a layered security approach, which involves implementing multiple security measures to protect against various types of threats. This approach includes using firewalls, intrusion detection systems, antivirus software, and encryption to safeguard data. By layering these security measures, individuals and organizations can significantly reduce the risk of a security breach.
2. Educating Users about Cybersecurity Best Practices
Steve Proud emphasizes the importance of educating users about cybersecurity best practices. This includes teaching users how to identify and avoid phishing emails, how to create strong passwords, and how to use two-factor authentication. By educating users, individuals and organizations can significantly reduce the risk of a security breach caused by human error.
Cybersecurity Best Practices for Users
- Use strong, unique passwords for all accounts
- Enable two-factor authentication whenever possible
- Be cautious when clicking on links or opening attachments from unknown sources
- Use antivirus software to scan for malware
- Regularly update software and operating systems
3. Conducting Regular Security Audits
Steve Proud recommends conducting regular security audits to identify vulnerabilities and weaknesses in security systems. These audits can help identify potential security risks and provide recommendations for mitigating those risks. By conducting regular security audits, individuals and organizations can stay ahead of potential threats and ensure their security systems are up-to-date.

4. Implementing Incident Response Plans
Steve Proud stresses the importance of implementing incident response plans in case of a security breach. These plans should outline the steps to take in the event of a breach, including containing the breach, eradicating the threat, and restoring systems. By having an incident response plan in place, individuals and organizations can minimize the impact of a security breach and reduce downtime.
Key Components of an Incident Response Plan
- Identification and containment of the breach
- Eradication of the threat
- Restoration of systems
- Communication with stakeholders and customers
- Post-incident review and improvement
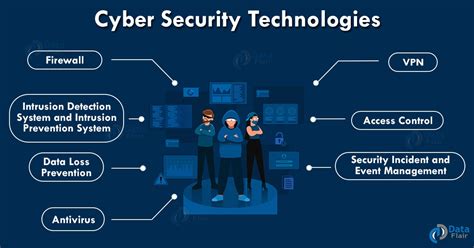
5. Staying Up-to-Date with the Latest Security Technologies
Finally, Steve Proud emphasizes the importance of staying up-to-date with the latest security technologies. This includes staying informed about new threats and vulnerabilities, as well as implementing new security technologies and solutions. By staying current with the latest security technologies, individuals and organizations can ensure their security systems are equipped to handle emerging threats.

Conclusion
Cybersecurity is a critical concern for individuals and organizations in today's digital age. Steve Proud's expertise and strategies can help strengthen cybersecurity and protect against emerging threats. By implementing a layered security approach, educating users about cybersecurity best practices, conducting regular security audits, implementing incident response plans, and staying up-to-date with the latest security technologies, individuals and organizations can significantly reduce the risk of a security breach.
Gallery of Cybersecurity Images
Cybersecurity Image Gallery








We hope this article has provided valuable insights into the importance of cybersecurity and the ways Steve Proud helps to strengthen it. By following these strategies and staying informed about the latest security technologies, individuals and organizations can significantly reduce the risk of a security breach and protect themselves from emerging threats.
