5 Steps To Create Nist 800-171 System Security Plan Summary
Implement a robust System Security Plan with our 5-step guide to NIST 800-171 compliance. Learn how to assess, develop, and maintain a secure system, ensuring Controlled Unclassified Information (CUI) protection. Streamline your security process with our actionable tips on risk management, access control, and incident response, and achieve compliance with confidence.
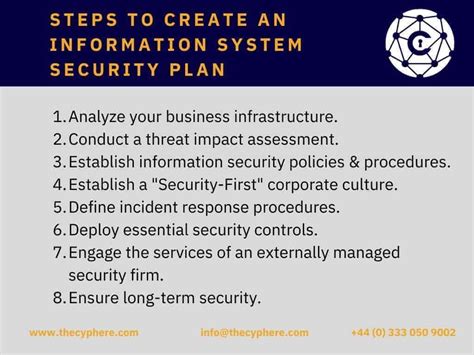
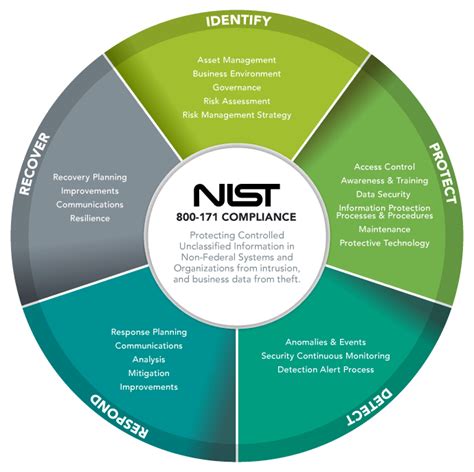
The National Institute of Standards and Technology (NIST) Special Publication 800-171 is a set of guidelines designed to protect the confidentiality, integrity, and availability of Controlled Unclassified Information (CUI) in non-federal information systems and organizations. Creating a System Security Plan (SSP) is a crucial step in implementing NIST 800-171 requirements. Here's a 5-step guide to help you create a comprehensive SSP:

Step 1: Define the Scope and Boundaries of the System
To create an effective SSP, you need to clearly define the scope and boundaries of the system that will be protected. This includes identifying the system's components, interfaces, and interconnections. You should also determine the types of CUI that will be stored, processed, or transmitted by the system.
- Identify the system's purpose and functionality
- Determine the system's boundaries, including hardware, software, and personnel
- Identify the types of CUI that will be handled by the system
- Document the system's components, interfaces, and interconnections
Step 2: Conduct a Risk Assessment
A risk assessment is essential to identify potential vulnerabilities and threats to the system. This step helps you understand the likelihood and impact of a security breach, which informs the development of your SSP.
- Identify potential threats to the system, including insider threats, cyber attacks, and environmental hazards
- Assess the vulnerabilities of the system, including technical, administrative, and physical vulnerabilities
- Determine the likelihood and impact of a security breach
- Document the risk assessment results and recommendations
Step 3: Develop Security Controls
Based on the risk assessment, you'll need to develop security controls to mitigate or eliminate identified risks. NIST 800-171 provides a set of security controls that you can use as a starting point.
- Select and tailor security controls to address identified risks
- Ensure that security controls are aligned with NIST 800-171 requirements
- Document the security controls, including their implementation and maintenance

Step 4: Implement and Document Security Controls
Once you've developed the security controls, you'll need to implement and document them. This step includes configuring systems, training personnel, and maintaining documentation.
- Implement security controls, including technical, administrative, and physical controls
- Document the implementation of security controls, including configuration settings and procedures
- Train personnel on the security controls and their roles and responsibilities
- Maintain documentation, including security plans, procedures, and records
Step 5: Monitor and Review the SSP
The final step is to monitor and review the SSP to ensure its effectiveness and compliance with NIST 800-171 requirements.
- Monitor the system for security incidents and vulnerabilities
- Review the SSP annually or as needed to ensure its continued effectiveness
- Update the SSP to reflect changes to the system or security controls
- Maintain documentation, including security incident response plans and procedures

By following these 5 steps, you can create a comprehensive SSP that meets NIST 800-171 requirements and protects your organization's CUI.
Gallery of NIST 800-171 System Security Plan
NIST 800-171 System Security Plan Image Gallery



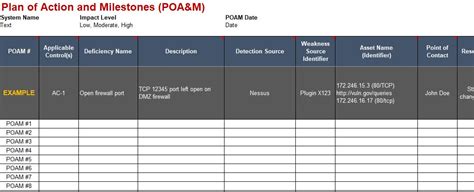


We hope this article has provided you with a comprehensive guide to creating a NIST 800-171 System Security Plan. If you have any questions or need further clarification, please don't hesitate to ask.
