Uncover the secret world of War Clandestine Twitter, where covert online battles rage between nation-states, hackers, and influencers. Explore the hidden battleground of cyberwarfare, disinformation, and propaganda, and discover how social media is reshaping modern conflict, national security, and global politics in this in-depth exposé.
In the digital age, warfare has transcended traditional borders and battlefields, extending into the realm of social media. Twitter, with its vast user base and real-time updates, has become a prime platform for clandestine warfare. The microblogging site has evolved into a hidden battleground where nations, organizations, and individuals engage in covert operations, seeking to influence public opinion, shape narratives, and disrupt adversaries. This phenomenon, known as the "War Clandestine Twitter," has significant implications for global politics, cybersecurity, and the future of warfare.
The Rise of Clandestine Twitter Warfare
The advent of social media has revolutionized the way nations and organizations conduct warfare. Twitter, with its character limit and hashtag-driven conversations, has become an ideal platform for clandestine operations. The site's algorithms and anonymous nature allow users to create fake accounts, spread disinformation, and engage in psychological warfare without being detected. This has led to a proliferation of covert Twitter operations, as nations and organizations seek to exploit the platform's potential for influence and disruption.
Types of Clandestine Twitter Operations
Clandestine Twitter operations can be broadly categorized into three types:
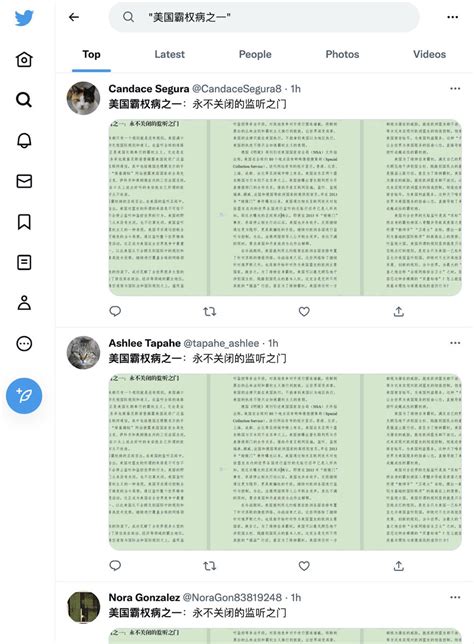
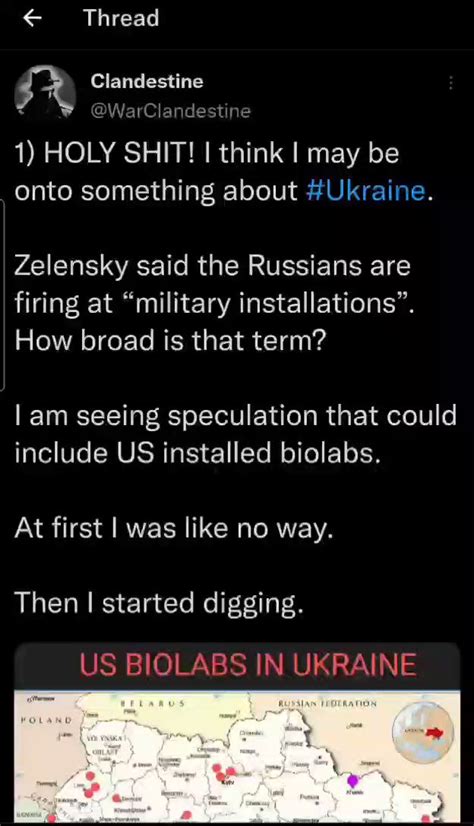
- Disinformation campaigns: These involve creating and disseminating false information to deceive or manipulate public opinion. Disinformation campaigns can be used to create confusion, undermine trust in institutions, or shape narratives to favor a particular agenda.
- Psychological operations: These aim to influence the emotions, motivations, and behaviors of target audiences. Psychological operations can be used to create fear, anxiety, or a sense of uncertainty, ultimately undermining the morale and cohesion of adversaries.
- Cyber reconnaissance: This involves using Twitter to gather intelligence on adversaries, monitor their activities, and identify vulnerabilities. Cyber reconnaissance can be used to inform future operations, anticipate potential threats, and develop countermeasures.
The Anatomy of a Clandestine Twitter Operation
A clandestine Twitter operation typically involves several key components:
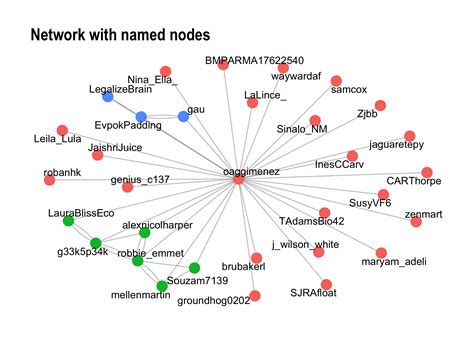
- Fake accounts: These are Twitter accounts created to disguise the true identity of the operator. Fake accounts can be used to spread disinformation, engage in psychological operations, or conduct cyber reconnaissance.
- Bots and trolls: These are automated or human-operated accounts used to amplify or disrupt messages. Bots and trolls can be used to create the illusion of widespread support or opposition, or to harass and intimidate adversaries.
- Hashtag campaigns: These involve using specific hashtags to promote or disrupt messages. Hashtag campaigns can be used to create trending topics, hijack conversations, or associate adversaries with unpopular or divisive issues.
- Influencer networks: These are networks of influential Twitter users who can be leveraged to amplify or promote messages. Influencer networks can be used to create the illusion of grassroots support or to associate adversaries with unpopular or divisive issues.
Case Studies: Clandestine Twitter Operations in Action
Several high-profile cases have highlighted the role of clandestine Twitter operations in modern warfare:
- Russian interference in the 2016 US presidential election: Russian operatives used Twitter to spread disinformation, engage in psychological operations, and disrupt the democratic process.
- Chinese information operations against Taiwan: Chinese operatives have used Twitter to spread disinformation, undermine trust in Taiwanese institutions, and promote a pro-China narrative.
- Iranian cyber operations against the US: Iranian operatives have used Twitter to conduct cyber reconnaissance, spread disinformation, and engage in psychological operations against US targets.
Countering Clandestine Twitter Operations

To counter clandestine Twitter operations, nations and organizations must adopt a multi-faceted approach:
- Enhanced social media monitoring: This involves monitoring Twitter for suspicious activity, tracking hashtags and keywords, and identifying potential disinformation campaigns.
- Cybersecurity measures: This includes implementing robust cybersecurity measures to protect against cyber reconnaissance and disrupt bot and troll networks.
- Influencer network analysis: This involves analyzing influencer networks to identify potential operatives and disrupt their activities.
- Public awareness and education: This includes educating the public on the risks of clandestine Twitter operations and promoting media literacy to counter disinformation campaigns.
Conclusion: The Future of Clandestine Twitter Warfare
The rise of clandestine Twitter warfare has significant implications for global politics, cybersecurity, and the future of warfare. As nations and organizations continue to exploit the platform's potential for influence and disruption, it is essential to develop effective countermeasures to mitigate these threats. By understanding the anatomy of clandestine Twitter operations and adopting a multi-faceted approach to countering them, we can promote a safer, more secure, and more transparent digital environment.
Clandestine Twitter Warfare Image Gallery