Intro
Unlock the secrets of Signal Intelligence! Discover how SIGINT intercepts and analyzes signals to uncover valuable intel. Learn about its types, methods, and applications in national security, cyber warfare, and more. Explore the importance of signal processing, communications intelligence, and electronic intelligence in the world of signals intelligence.
In today's world of advanced technology and global connectivity, the collection and analysis of signals has become a crucial aspect of modern intelligence gathering. Signal intelligence, or SIGINT, is a vital component of intelligence gathering that involves the interception, processing, and analysis of signals to extract valuable information. In this article, we will delve into the world of signal intelligence, exploring its history, types, methods, and applications.
History of Signal Intelligence
Signal intelligence has its roots in the early 20th century, when radio communication became a vital means of communication for military forces. During World War I, countries began intercepting and decoding enemy radio communications to gain strategic advantage. The British, in particular, developed a sophisticated system of radio interception and decryption, which played a significant role in the war.
In the aftermath of World War II, the United States and the Soviet Union emerged as superpowers, and signal intelligence became an essential tool for gathering intelligence on each other's military capabilities and intentions. The National Security Agency (NSA) was established in 1952 to oversee the collection and analysis of signal intelligence in the United States.
Types of Signal Intelligence
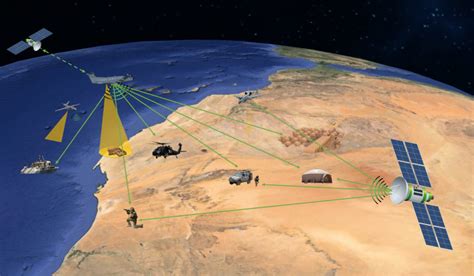
Signal intelligence can be broadly categorized into two types: communications intelligence (COMINT) and electronic intelligence (ELINT).
- Communications Intelligence (COMINT): COMINT involves the interception and analysis of communication signals, such as radio transmissions, emails, and phone calls. This type of intelligence is used to gather information on an adversary's communication patterns, networks, and technologies.
- Electronic Intelligence (ELINT): ELINT involves the collection and analysis of non-communication signals, such as radar emissions, telemetry data, and other electronic emissions. This type of intelligence is used to gather information on an adversary's military capabilities, such as the location and characteristics of radar systems.
Methods of Signal Intelligence Collection

Signal intelligence can be collected using a variety of methods, including:
- Intercepting radio transmissions and other communication signals
- Monitoring electronic emissions, such as radar and telemetry data
- Analyzing communication patterns and networks
- Using satellite-based systems to collect signal intelligence
- Employing human intelligence (HUMINT) sources to gather information on an adversary's signal intelligence capabilities
Applications of Signal Intelligence
Signal intelligence has a wide range of applications, including:
- Military operations: Signal intelligence is used to gather information on an adversary's military capabilities, such as the location and characteristics of radar systems and communication networks.
- National security: Signal intelligence is used to identify and disrupt terrorist organizations and other threats to national security.
- Law enforcement: Signal intelligence is used to gather information on organized crime and other law enforcement targets.
- Economic intelligence: Signal intelligence is used to gather information on an adversary's economic capabilities and intentions.
Techniques of Signal Intelligence Analysis

Signal intelligence analysis involves a range of techniques, including:
- Traffic analysis: This involves analyzing communication patterns and networks to identify trends and anomalies.
- Cryptanalysis: This involves decrypting encrypted signals to extract valuable information.
- Direction finding: This involves using specialized equipment to locate the source of a signal.
- Signal processing: This involves using algorithms and software to process and analyze signal intelligence data.
Challenges of Signal Intelligence
Signal intelligence faces a range of challenges, including:
- Encryption: The increasing use of encryption has made it more difficult to intercept and analyze signal intelligence.
- Big data: The vast amounts of signal intelligence data being generated every day pose significant challenges for analysts.
- Cybersecurity: The threat of cyber attacks and data breaches has made it essential to prioritize cybersecurity in signal intelligence operations.
Future of Signal Intelligence

The future of signal intelligence will be shaped by advances in technology and the evolving threat landscape. Some of the key trends that will shape the future of signal intelligence include:
- Artificial intelligence: The increasing use of artificial intelligence and machine learning algorithms will enhance the analysis and processing of signal intelligence data.
- Cloud computing: The use of cloud computing will enable the storage and analysis of large amounts of signal intelligence data.
- Cybersecurity: The threat of cyber attacks and data breaches will continue to prioritize cybersecurity in signal intelligence operations.
Gallery of Signal Intelligence Images
Signal Intelligence Image Gallery






Conclusion
Signal intelligence is a vital component of modern intelligence gathering, providing valuable information on an adversary's military capabilities, communication patterns, and intentions. From its early beginnings in World War I to the present day, signal intelligence has evolved significantly, driven by advances in technology and the changing threat landscape. As we move forward, it is essential to prioritize cybersecurity, invest in artificial intelligence and machine learning, and adapt to the evolving threat landscape to ensure the continued effectiveness of signal intelligence operations.
We hope this article has provided you with a comprehensive understanding of signal intelligence and its applications. If you have any questions or would like to learn more, please leave a comment below.
