Intro
Streamline compliance with our 7 essential NIST 800-53 policy templates. Ensure robust security and risk management with these customizable templates, covering access control, incident response, and more. Simplify your NIST 800-53 implementation and improve compliance with these expert-crafted policy templates, perfect for federal agencies and contractors.
NIST 800-53 Policy Templates: Streamlining Your Compliance Efforts

In today's increasingly complex cybersecurity landscape, organizations face numerous challenges in protecting their sensitive data and systems. The National Institute of Standards and Technology (NIST) provides a framework for managing risk and ensuring compliance with various regulations and standards. NIST Special Publication 800-53 (Rev. 4) outlines a comprehensive set of controls for securing federal information systems. However, implementing these controls can be overwhelming, especially for smaller organizations with limited resources.
Fortunately, using NIST 800-53 policy templates can significantly simplify the process of developing and maintaining effective security policies. These templates provide pre-drafted policy language and frameworks that organizations can tailor to their specific needs, ensuring they stay compliant with NIST requirements.
Understanding NIST 800-53 Policy Templates
NIST 800-53 policy templates are designed to help organizations implement the security controls outlined in the NIST 800-53 standard. These templates typically cover the following areas:
- Policy statement: A high-level overview of the organization's commitment to security and compliance.
- Purpose: A brief explanation of the purpose of the policy.
- Scope: A description of the policy's scope, including the individuals and systems affected.
- Roles and responsibilities: A definition of the roles and responsibilities of personnel involved in implementing and enforcing the policy.
- Policy content: Detailed policy language outlining the specific requirements and controls.
7 Essential NIST 800-53 Policy Templates

Here are seven essential NIST 800-53 policy templates that can help organizations streamline their compliance efforts:
1. Incident Response Policy Template
An incident response policy template outlines the procedures for responding to security incidents, such as data breaches or malware outbreaks. This template should cover the following:
- Incident response plan: A detailed plan for responding to incidents, including incident classification, containment, and eradication.
- Roles and responsibilities: A definition of the roles and responsibilities of incident response team members.
- Incident reporting: Procedures for reporting incidents to management, law enforcement, and other relevant parties.
2. Access Control Policy Template
An access control policy template defines the procedures for controlling access to sensitive systems and data. This template should cover the following:
- Access control principles: A statement of the organization's access control principles, including the concept of least privilege.
- Access control procedures: Detailed procedures for granting, revoking, and managing access to systems and data.
- Access control technologies: A description of the access control technologies used, such as passwords, smart cards, and biometric authentication.
3. Configuration Management Policy Template
A configuration management policy template outlines the procedures for managing changes to systems and software. This template should cover the following:
- Configuration management principles: A statement of the organization's configuration management principles, including the concept of change control.
- Change management procedures: Detailed procedures for requesting, reviewing, and approving changes to systems and software.
- Configuration management tools: A description of the configuration management tools used, such as version control systems and patch management software.
4. Data Backup and Recovery Policy Template
A data backup and recovery policy template defines the procedures for backing up and recovering sensitive data. This template should cover the following:
- Data backup principles: A statement of the organization's data backup principles, including the concept of redundancy.
- Data backup procedures: Detailed procedures for backing up sensitive data, including frequency, retention, and storage.
- Data recovery procedures: Detailed procedures for recovering data in the event of a disaster or system failure.
5. Network Security Policy Template
A network security policy template outlines the procedures for securing network communications and infrastructure. This template should cover the following:
- Network security principles: A statement of the organization's network security principles, including the concept of defense-in-depth.
- Network security procedures: Detailed procedures for securing network communications, including encryption, firewalls, and intrusion detection.
- Network security technologies: A description of the network security technologies used, such as VPNs, routers, and switches.
6. Personnel Security Policy Template
A personnel security policy template defines the procedures for managing personnel security, including background checks, training, and awareness. This template should cover the following:
- Personnel security principles: A statement of the organization's personnel security principles, including the concept of trustworthiness.
- Background check procedures: Detailed procedures for conducting background checks on employees, contractors, and third-party vendors.
- Security awareness and training: Procedures for providing security awareness and training to personnel.
7. Vulnerability Management Policy Template
A vulnerability management policy template outlines the procedures for identifying, assessing, and remediating vulnerabilities in systems and software. This template should cover the following:
- Vulnerability management principles: A statement of the organization's vulnerability management principles, including the concept of risk-based remediation.
- Vulnerability identification procedures: Detailed procedures for identifying vulnerabilities, including vulnerability scanning and penetration testing.
- Vulnerability remediation procedures: Detailed procedures for remediating vulnerabilities, including patch management and configuration changes.
Implementing NIST 800-53 Policy Templates
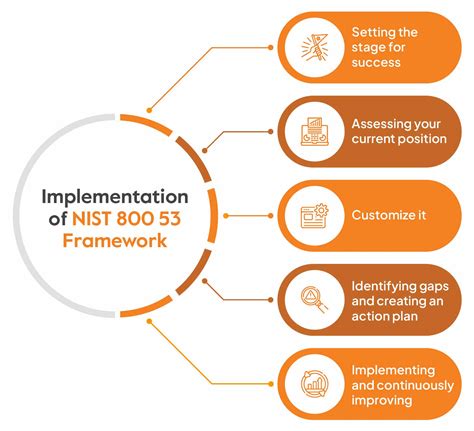
Implementing NIST 800-53 policy templates requires a thorough understanding of the organization's security requirements and the NIST 800-53 standard. Here are some steps to follow:
- Conduct a risk assessment: Identify the organization's security risks and vulnerabilities to determine the necessary controls.
- Select relevant templates: Choose the policy templates that align with the organization's security requirements.
- Tailor the templates: Customize the templates to fit the organization's specific needs, including policies, procedures, and controls.
- Review and approve: Review and approve the policy templates to ensure they meet the organization's security requirements.
- Implement and enforce: Implement the policy templates and enforce them through regular monitoring, auditing, and training.
Conclusion
In conclusion, using NIST 800-53 policy templates can significantly simplify the process of developing and maintaining effective security policies. By understanding the essential policy templates and implementing them, organizations can ensure compliance with NIST requirements and protect their sensitive data and systems.
NIST 800-53 Policy Templates Image Gallery








Feel free to share your thoughts on NIST 800-53 policy templates in the comments below. If you have any questions or need further clarification on implementing these templates, please don't hesitate to ask.
