Intro
Protect your network from malicious threats by mitigating security risks from Excel macros. Learn how to detect, prevent, and remove macro-based malware with ease. Discover best practices for securing your spreadsheets, including macro settings, VBA code review, and user education. Ensure data integrity and safeguard your organizations sensitive information.
The widespread use of Microsoft Excel in various industries has led to an increased reliance on Excel macros to automate repetitive tasks, simplify complex processes, and enhance productivity. However, the very feature that makes macros so powerful also makes them a potential security risk. In this article, we will delve into the world of Excel macros, explore the security risks associated with them, and provide actionable tips on how to mitigate these risks with ease.
The Power and Peril of Excel Macros
Excel macros are essentially small programs that automate tasks within a spreadsheet. They can be used to perform a wide range of tasks, from simple data manipulation to complex calculations and reporting. Macros are often used to save time, reduce errors, and improve efficiency. However, they can also pose a significant security risk if not properly managed.
One of the primary security risks associated with Excel macros is the potential for malicious code to be embedded within them. This can happen when a macro is downloaded from an untrusted source or when a user unknowingly enables macros from a malicious file. Once a malicious macro is executed, it can compromise the security of the entire system, leading to data breaches, financial losses, and reputational damage.

Understanding the Security Risks of Excel Macros
To mitigate the security risks associated with Excel macros, it is essential to understand the types of risks that exist. Some of the most common security risks associated with Excel macros include:
- Malware: Macros can be used to spread malware, such as viruses, Trojans, and ransomware.
- Data breaches: Macros can be used to steal sensitive data, such as financial information, personal identifiable information (PII), and confidential business data.
- System compromise: Macros can be used to gain unauthorized access to a system, leading to system compromise and potential data breaches.
- Denial of Service (DoS): Macros can be used to launch DoS attacks, which can render a system or network unavailable.
Mitigating Security Risks from Excel Macros
While the security risks associated with Excel macros are real, there are steps that can be taken to mitigate these risks. Here are some actionable tips on how to mitigate security risks from Excel macros with ease:
Enable Macro Security Settings
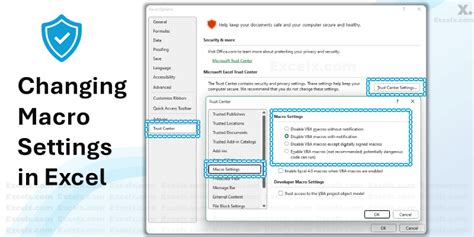
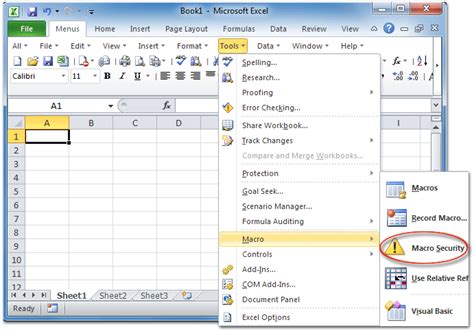
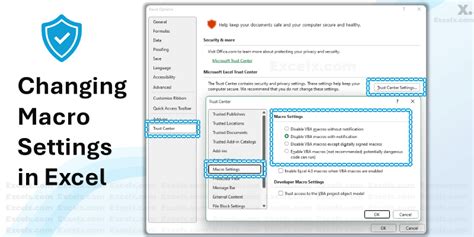
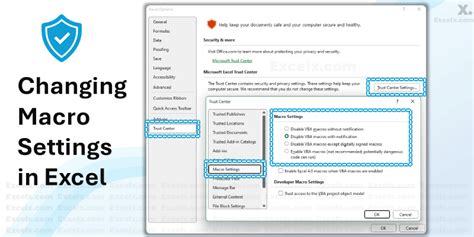
One of the simplest ways to mitigate security risks from Excel macros is to enable macro security settings. This can be done by going to the "Trust Center" settings in Excel and selecting the "Macro Settings" option.
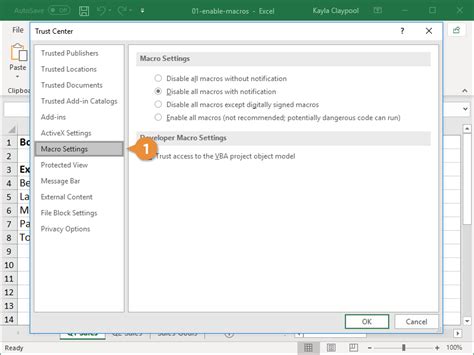
Use Digital Signatures
Using digital signatures is another effective way to mitigate security risks from Excel macros. Digital signatures can be used to authenticate the source of a macro and ensure that it has not been tampered with.
Validate Macro Sources
Validating macro sources is critical to ensuring that only trusted macros are executed. This can be done by verifying the source of a macro and ensuring that it is from a trusted provider.
Use Macro-Free Alternatives
Whenever possible, use macro-free alternatives to automate tasks in Excel. This can include using formulas, pivot tables, and other built-in Excel features.
Implement Macro Whitelisting
Implementing macro whitelisting is another effective way to mitigate security risks from Excel macros. This involves creating a list of trusted macros that are allowed to run on a system.
Provide User Training
Providing user training is critical to ensuring that users understand the security risks associated with Excel macros and how to mitigate these risks.
Best Practices for Secure Macro Development
When developing macros, there are several best practices that can be followed to ensure that they are secure. Some of these best practices include:
Use Secure Coding Practices
Using secure coding practices is critical to ensuring that macros are secure. This includes using secure coding techniques, such as input validation and error handling.
Test Macros Thoroughly
Testing macros thoroughly is essential to ensuring that they are secure and function as intended.
Use Secure Data Storage
Using secure data storage is critical to ensuring that sensitive data is protected. This includes using secure data storage techniques, such as encryption.
Implement Access Controls
Implementing access controls is essential to ensuring that only authorized users can access and execute macros.
Gallery of Excel Macro Security Images
Excel Macro Security Images




Conclusion
Mitigating security risks from Excel macros requires a proactive approach that involves understanding the risks, implementing security measures, and following best practices for secure macro development. By following the tips and best practices outlined in this article, you can ensure that your Excel macros are secure and function as intended.
We hope this article has provided you with valuable insights into the security risks associated with Excel macros and how to mitigate these risks. If you have any questions or comments, please feel free to share them with us.
