Unlock the secrets of the alphabet with Alpha Codes. Discover the hidden meanings behind the 26 secret call letters, also known as phonetic alphabets or NATO codes. Learn how to decipher and use these codes for clear communication, from aviation and military to everyday use. Explore the fascinating world of Alpha Codes and improve your understanding of this essential communication tool.
In the world of communication, codes, and secret messages, there exists a fascinating system of letter substitution that has been used for centuries. Alpha codes, also known as alphabetical codes or substitution ciphers, are a way of replacing letters with other letters or symbols to conceal the meaning of a message. In this article, we will delve into the world of alpha codes, exploring their history, types, and uses, as well as providing examples and tips for creating and deciphering these secret call letters.
History of Alpha Codes

The use of alpha codes dates back to ancient civilizations, where they were used for secure communication and encryption. One of the earliest known examples of an alpha code is the Caesar Cipher, used by Julius Caesar to communicate with his generals during the Gallic Wars. This simple substitution cipher involved shifting each letter by a fixed number of positions in the alphabet.
Throughout history, alpha codes have been used for various purposes, including military communication, diplomacy, and even literary works. For example, the famous novelist, Edgar Allan Poe, was known to use alpha codes in his stories and poems.
Types of Alpha Codes
There are several types of alpha codes, each with its own unique characteristics and uses. Some common types of alpha codes include:
- Substitution ciphers: These codes involve replacing each letter with a different letter or symbol.
- Transposition ciphers: These codes involve rearranging the letters of the original message.
- Vigenère ciphers: These codes use a series of Caesar ciphers with different shifts for each letter.
How Alpha Codes Work
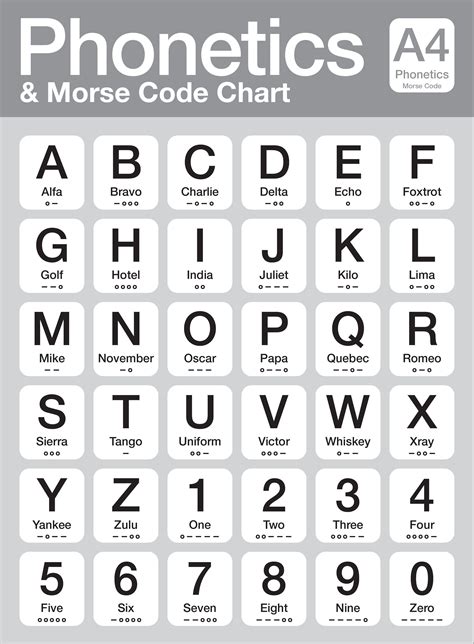
Alpha codes work by replacing each letter of the original message with a different letter or symbol. This can be done using a variety of techniques, including substitution, transposition, and Vigenère ciphers.
For example, a simple substitution cipher might replace each letter with a letter a fixed number of positions ahead of it in the alphabet. So, the letter "a" might be replaced with the letter "d", the letter "b" with the letter "e", and so on.
Creating an Alpha Code
Creating an alpha code is a simple process that can be done using a variety of techniques. Here are the steps to create a basic substitution cipher:
- Choose a key or password to use for the cipher.
- Create a substitution chart or table that shows the original letter and its corresponding substitute.
- Use the chart to substitute each letter of the original message.
For example, let's create a simple substitution cipher using the key "code". We can create a substitution chart as follows:
| Original Letter | Substitute |
|---|---|
| a | c |
| b | o |
| c | d |
| d | e |
| e | f |
Using this chart, we can substitute each letter of the original message with its corresponding substitute.
Deciphering an Alpha Code
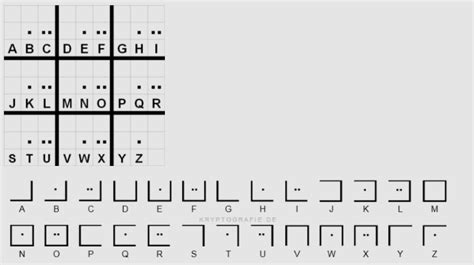
Deciphering an alpha code involves reversing the substitution process to reveal the original message. This can be done using a variety of techniques, including frequency analysis and cryptanalysis.
Frequency analysis involves analyzing the frequency of each letter in the cipher text to determine the most common letters and their corresponding substitutes. This can be used to create a frequency chart that shows the frequency of each letter in the cipher text.
Cryptanalysis involves using mathematical techniques to analyze the cipher text and determine the key or password used to create the cipher.
Tips for Creating and Deciphering Alpha Codes
Here are some tips for creating and deciphering alpha codes:
- Use a secure key or password to create the cipher.
- Use a variety of techniques, including substitution, transposition, and Vigenère ciphers.
- Analyze the frequency of each letter in the cipher text to determine the most common letters and their corresponding substitutes.
- Use mathematical techniques, such as cryptanalysis, to analyze the cipher text and determine the key or password.
Real-World Applications of Alpha Codes
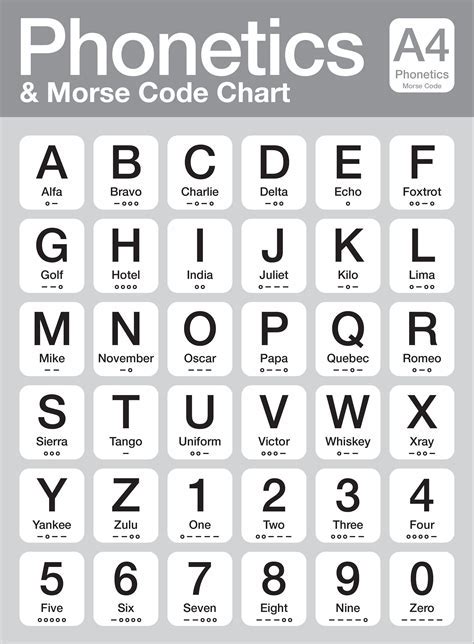
Alpha codes have a variety of real-world applications, including:
- Secure communication: Alpha codes can be used to create secure communication systems, such as encrypted email and messaging apps.
- Cryptography: Alpha codes are used in cryptography to create secure encryption algorithms, such as AES and RSA.
- Steganography: Alpha codes can be used to hide secret messages in images and other digital media.
Examples of Alpha Codes in Literature and History
Alpha codes have been used in literature and history to create secret messages and codes. Here are a few examples:
- The Caesar Cipher: Julius Caesar used the Caesar Cipher to communicate with his generals during the Gallic Wars.
- The Vigenère Cipher: This cipher was used by the French diplomat, Charles Vigenère, to create a secure communication system.
- The Zimmermann Telegram: This famous telegram was used by the German government during World War I to communicate with Mexico and persuade them to declare war on the United States.
Alpha Code Image Gallery


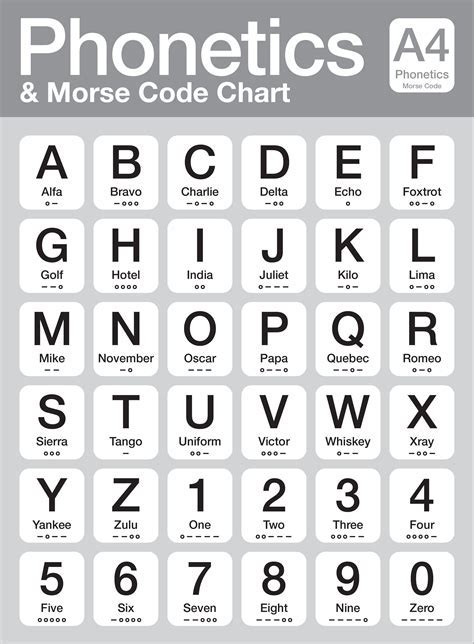





Conclusion and Final Thoughts
In conclusion, alpha codes are a fascinating world of letter substitution and secret messages. From the Caesar Cipher to the Vigenère Cipher, these codes have been used throughout history to create secure communication systems and conceal secret messages. Whether you're a cryptographer, a historian, or simply a curious individual, alpha codes offer a fascinating glimpse into the world of cryptography and secret communication.
